Is your data more secure than a decade ago? Over the development of the digital age, cybersecurity has changed from a technical concern to a vital part of online life. A study by Cybersecurity Ventures predicts cybercrime damages will cost the world $10.5 trillion annually by 2025, marking an unprecedented era of digital vulnerability.
This staggering figure underscores how active cybercriminals are and how impactful a breach can be, with one potentially affecting millions. In this climate, understanding the scale and scope of cyber threats is not just informative—it's critical for collective defense.
10 Alarming Cybercrime Statistics in 2024
1. Increase in Cybercrime Incidents
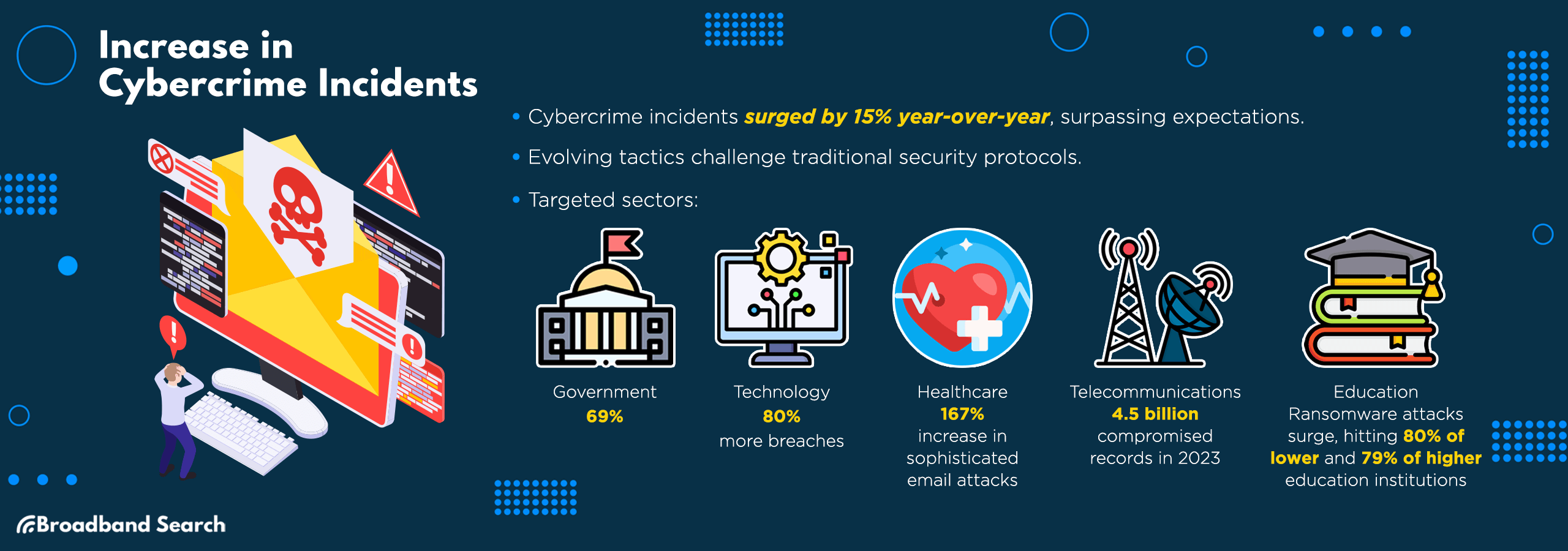
A comparative study shows cybercrime incidents have climbed by 15 percent year-over-year, marking a stark escalation from 2022, surpassing previous suggestions.
Yet it’s not just numbers. The threats themselves are changing. Tactics employed are increasingly insidious, often outsmarting traditional security protocols. As the digital realm evolves, so does the cybercriminals' arsenal.
Most Targeted Sectors
- Government and Administration: Bearing the brunt with 69 percent, this sector’s high-value data makes it a prime target, stressing the need for robust security protocols to safeguard national interests and citizen privacy.
- Technology: Representing the frontline of digital innovation, the technology sector's breach statistics have swelled by 80 percent.
- Healthcare: The healthcare sector has seen a 167 percent rise in sophisticated email attacks this year, including business email compromise attacks, credential phishing, malware, and extortion.
- Telecommunications: Recent findings show that September of last year had 71 public security breaches involving 3.8 billion compromised records, pushing the year's total past 4.5 billion. And when the telecommunications sector is successfully attacked, everyone is affected.
- Education: Ransomware attacks have surged in education, with 80 percent of lower and 79 percent of higher education institutions hit last year, marking a stark increase from 44 percent in 2021 and highlighting ransomware as education’s foremost cyber threat.
2. Ransomware Attacks on the Rise
Number of Attacks and High-Profile Cases
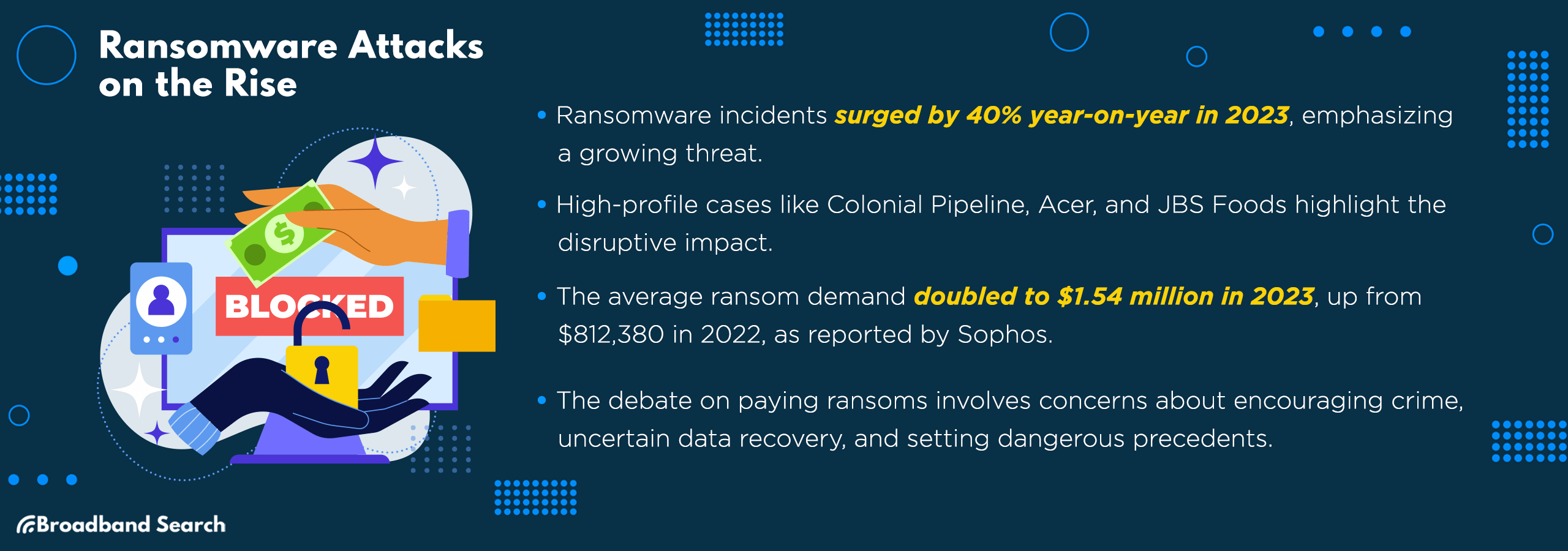
Ransomware's grip on victims has tightened in the past year, with incidents skyrocketing by an alarming 40 percent year-on-year. Attackers aren't just encrypting data but now engaging in "double extortion," threatening to publish stolen data unless additional demands are met.
Some high-profile cases exemplifying the severity of the problem include:
- Colonial Pipeline (2021): One of the most disruptive ransomware attacks targeted the Colonial Pipeline, causing widespread fuel shortages and elevating the discourse on infrastructure vulnerability.
- Acer (2021): Acer experienced a staggering $50 million ransom demand, the largest known at the time. Even tech giants are not immune from these threats.
- JBS Foods (2021): The world's largest meat producer, JBS Foods, suffered an attack disrupting global operations and the supply chain. Cyber attacks can affect things as essential as food security.
These are only examples, but they showcase the need for improved measures against ransomware in the years to come.
Average Ransom Amount
The average ransom demand by cybercriminals has swelled to $1.54 million, nearly doubling from $812,380 in 2022, according to Sophos.
Should companies pay ransoms? Paying ransoms fuels a contentious debate involving the following factors:
- Encouragement of Crime: Payment is seen as funding and encouraging further criminal activities.
- No Guarantee of Data Recovery: Paying the ransom only sometimes results in data recovery, leading to funds being expended with no return.
- Setting a Dangerous Precedent: Complying with ransom demands sets a precedent, potentially making the organization a repeat target.
This intricate issue spotlights many organizations' no-win scenario, forcing a choice between an immediate resolution and a principled stand against funding cybercrime.
3. Phishing Attacks Remain Prevalent
Percentage of Total Cybercrimes
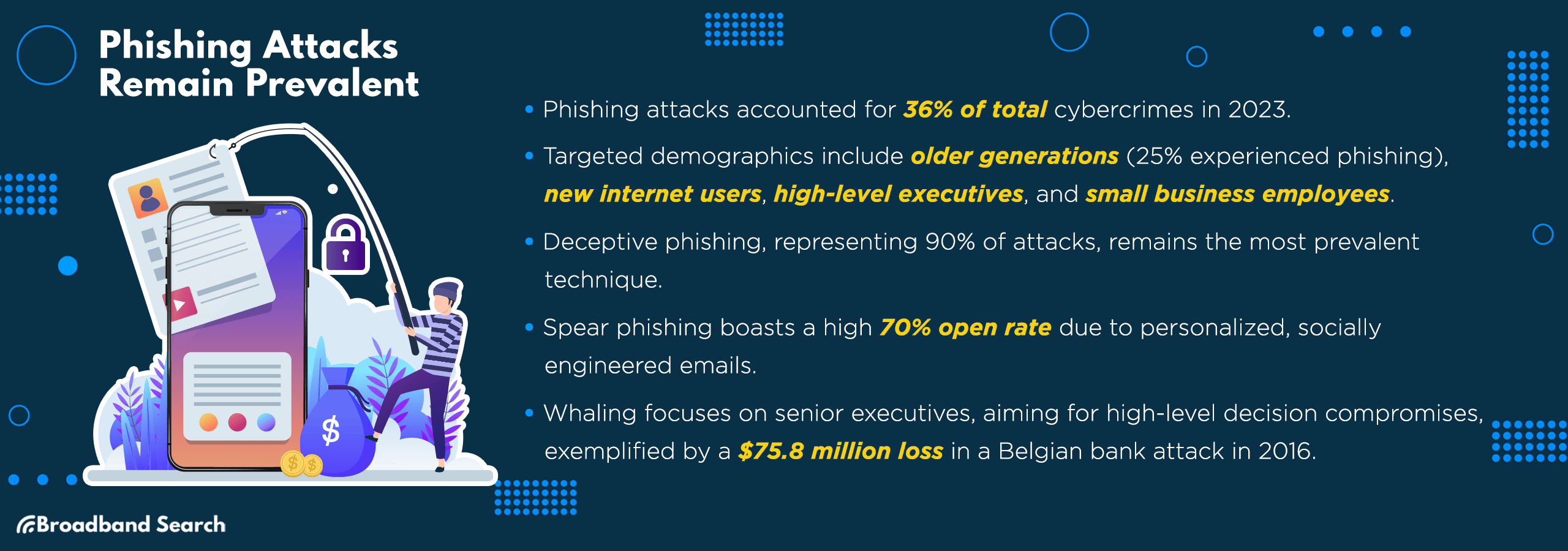
Phishing attacks, the deceptive art of extracting sensitive information under false pretenses, have evolved. In the past year, they represented an alarming 36 percent of total cybercrimes.
Most Targeted Demographics
- Older Generations: Less familiarity with digital nuances makes them prime targets, with one in four people over the age of 60 experiencing phishing attempts.
- New Internet Users: New internet users need more experience to recognize more obvious traps.
- High-Level Executives: With access to critical corporate information, C-suite executives are desirable targets for spear-phishing attacks.
- Small Business Employees: Small businesses often have less stringent cybersecurity, making their employees low-hanging fruit for attackers.
Most Common Phishing Techniques
- Deceptive Phishing: The most common form, deceptive phishing, masquerades as legitimate communication from reputable entities to steal user data. A staggering 90 percent of phishing attacks in the past year fell into this category, demonstrating its continued effectiveness.
- Spear Phishing: Spear phishing targets specific individuals and is more personalized. Latest figures indicate a 70 percent open rate for these meticulously crafted emails, as cybercriminals use social engineering to tailor their deceptive emails with alarming precision.
- Whaling: A form of spear phishing, whaling targets the 'big fish' — senior executives. In 2016, a $75.8 million loss was reported to a Belgian bank, aiming to compromise high-level decisions and financial transfers.
- Smishing (SMS Phishing): Using text messages, smishing attacks have jumped 300 percent since 2020. These SMS messages often contain malicious links.
- Pharming: Cybercriminals use pharming to redirect users from legitimate websites to fraudulent ones. Pharming attacks cost organizations over $50 million in financial losses in 2021.
4. Economic Impact of Cybercrimes

Global Losses
The economic shockwaves of cybercrime in the past year have been staggering, with global losses estimated to surpass $8 trillion, an ominous rise from previous tallies.
The economic onslaught of cybercrime extends beyond immediate financial losses, resonating through a complex web of direct and indirect costs. Companies grapple with diminished productivity and tarnished reputations while pouring resources into recovery.
- United States: Estimated losses surpassed $10 billion in 2022, underscoring the high stakes of cyber threats in the world's largest economy.
- Europe: With losses amounting to €5.5 trillion at the end of 2020, Europe's diverse cyber landscape reflects its nations' varying cyber defense effectiveness.
- Asia: Asia reported a staggering $10.3 billion in cybercrime-related economic damage.
5. Increase in Insider Threats
Percentage of Internal vs. External Attacks
Insider threats, a formidable and often overlooked danger, have risen alarmingly, constituting up to 34 percent of all cyber incidents. These attacks are especially pernicious due to their exploitation of trust and access.
Types of Insider Threats
- Espionage: Individuals who sell or trade stolen intellectual property or confidential information. Example: An engineer at a car manufacturer transmits designs to a competitor for payment, undermining years of R&D efforts and reducing competitiveness.
- Fraud: Insider fraud, representing 20 percent of such threats, includes embezzlement or data manipulation, leading to financial losses and undermining stakeholder trust.
- Terrorism: Rare but devastating, this involves insiders inflicting damage to further ideological goals. Imagine, for example, an IT employee at a defense contractor sabotaged military equipment software, jeopardizing national security.
- Theft: The simple act of stealing data or physical devices. A recent case involved a salesperson taking a client database to a new employer, directly harming sales and customer trust.
- Negligent Insider: Unintentional but common, negligent insiders cause about 56 percent of incidents due to carelessness, leading to data breaches and compliance violations. Human error is the most significant cause of data breaches.
The damage potential of insider threats is often more significant than external attacks due to the insider's legitimate access to sensitive areas. Consequently, the impact of such breaches can be devastating both financially and reputationally.
Motivations Behind Insider Threats
The motivations driving employees to commit cybercrimes are complex and varied, with repercussions that can be both far-reaching and highly damaging to an organization.
Reasons for Insider Cybercrimes
- Financial Gain: The most common motivator, where employees exfiltrate sensitive data to sell or exploit, contributing to a reported 47 percent of insider-related breaches.
- Revenge: Disgruntled employees may seek retribution, resulting in intentional harm to an organization’s data or systems, accounting for 14 percent of insider incidents.
- Recognition & Achievement: Some insiders, craving acknowledgment, might manipulate data or systems to enhance performance metrics, skewing business decisions and integrity.
- Sabotage: Acts of deliberate destruction or disruption from within have significant operational impacts, accounting for a costly eight percent of internal threats.
Best Practices for Mitigating Insider Threats:
- Comprehensive Auditing: Implementing regular system audits can identify unusual activities that may indicate insider threats, helping to prevent potential breaches.
- Positive Workplace Culture: Cultivating a positive work environment reduces the risk of disgruntlement and consequent insider threats, making it easier to spot changes in employee behavior.
- Employee Training: Regular training can minimize accidental breaches, equipping staff with the knowledge to recognize and avoid potential threats.
- Least Privilege Access: Limiting access rights to the minimum required for job functions reduces insider misuse or theft opportunities.
6. Exploitation of Remote Work
Cyberattacks on Home Networks
The swift shift to remote work has extended corporate perimeters directly into the more vulnerable terrain of home networks. These networks have become ripe targets without the robust defenses typically found in enterprise environments. A recent study indicated that 20 percent of home networks have misconfigured firewalls and 60 percent of remote workers use personal devices to access work systems, presenting attackers with low-hanging fruit.
Here are the five types of exploits most commonly observed in remote work scenarios:
- Unsecured Wi-Fi Networks: With 25 percent of home networks using weak encryption or none at all, hackers can easily intercept data, leading to information theft and unauthorized network access.
- Use of Personal Devices: BYOD (Bring Your Own Device) policies expand the attack surface, with 48 percent of cybersecurity incidents involving employee carelessness that lack professional security controls.
- Phishing Attacks: Exploiting remote communication, phishing attacks have surged by 22 percent, preying on isolated employees more likely to click on deceptive links.
- Inadequate Endpoint Security: Home devices lack comprehensive endpoint security, leading to a 75 percent increase in endpoint attacks as cybercriminals exploit less-protected personal equipment.
- Poor Patch Management: Delayed updates on personal devices have become a significant issue, with statistics showing a 20 percent increase in successful exploits of outdated software among remote workers.
The data points to a critical need for enhanced cybersecurity measures tailored for the remote workforce, emphasizing that the protective perimeter of IT security must now extend into each employee's home.
Unsecured Devices and Networks
The global shift towards remote work has thrust device management strategies to the forefront of cybersecurity priorities. With 92 percent of the workforce operating remotely at least once a week, managing devices becomes not just a matter of convenience but a linchpin of organizational security. A survey by Cisco Umbrella revealed that 46 percent of organizations experienced mobile device-related breaches.
The bedrock of remote work security is robust cybersecurity hygiene. These practices for remote workers must become as essential as locking the door at home:
- Robust VPN Use: VPNs cloak internet activity, making remote connections secure. A study showed a 54 percent decrease in breaches when companies mandated VPN use for all remote interactions.
- Regular Software Updates: Outdated applications are ripe for exploitation. An updated compliance policy reduced exploit-based attacks by 50 percent in surveyed firms.
- Multi-Factor Authentication (MFA): Companies using MFA saw a 50 percent drop in account compromise incidents.
- Secure Wi-Fi Access: Encrypted Wi-Fi with WPA3 security, rarely seen in home environments, can significantly reduce unauthorized access, an issue in 30 percent of remote work-related breaches in 2021.
- Data Encryption: Encrypting sensitive data reduces the cost of a data breach by an average of $360,000, according to IBM Security.
7. Growing Use of AI in Cyberattacks

AI-Driven Attack Methods
Artificial intelligence has ushered in a new era in the digital world. Cybercriminals are now leveraging AI to orchestrate more sophisticated and insidious attacks. Consider the following AI-related statistics:
- Deepfake Phishing: By utilizing AI to create convincing fake audio and video, deepfake phishing attacks have seen a 66 percent rise. A notable instance is the CEO voice deepfake scam that swindled $243,000 from a UK-based energy firm.
- AI-powered Malware: Customized AI algorithms have escalated malware effectiveness by 30 percent, allowing it to learn and adapt to security measures in real-time, evading detection longer than traditional malware, as seen in the evolution of polymorphic threats.
- Automated Brute-Force Attacks: AI has increased the frequency of brute-force attacks by 32 percent by reducing the time needed for an attack. The GitHub incident, where hundreds of repositories were compromised, is a stark reminder of their potency.
- Social Engineering Campaigns: AI's role in tailoring deceptive social engineering campaigns has grown by 90 percent, manipulating individual behavior with unprecedented precision.
- Supply Chain Attacks: Leveraging AI, cybercriminals can analyze vast amounts of data to identify the weakest link in a supply chain. One report attributed a 200 percent increase in supply chain attacks to the utilization of AI for vulnerability discovery.
Defensive AI Solutions
AI can be used for defense as well as crime. Here are five cutting-edge examples that exemplify the proactive shield AI has become:
- Automated Threat Detection Systems: These systems utilize machine learning to sift through millions of events daily, with one such tool by Darktrace detecting 74 percent more threats than traditional software.
- AI-based Behavioral Analytics: Tools like Exabeam use AI to establish a baseline of normal behavior for each user and device, allowing for detecting anomalies with a proven accuracy of 95 percent.
- Predictive AI Threat Intelligence: Platforms such as Recorded Future employ machine learning to scour the web, predicting and prioritizing potential threats. In the past year, such tools have improved threat anticipation timelines by up to 10 days, providing critical lead time for response teams.
- Automated Incident Response: Solutions like IBM’s Watson for Cyber Security can orchestrate and automate incident response processes, which has cut down resolution times from hours to minutes in simulated environments.
- AI-Enhanced Network Security: Cisco's AI Network Analytics applies machine learning to network data, enhancing visibility and security across the network. This has led to faster threat detection and remediation for its users.
8. Increase in Mobile Cyberattacks
Attack Types
Our reliance on mobile devices has rendered them attractive targets for cybercriminals, who have innovated and diversified their attack vectors. The data reflecting this trend not only captures the scope but also the sophistication of the threat. Here are five predominant mobile cyberattack types:
- Malicious Apps: These apps constitute a staggering 73 percent of mobile threats, stealing personal data or conscripting devices into botnets upon download.
- Man-in-the-Middle Attacks on Public Wi-Fi: Public Wi-Fi's convenience is its Achilles' heel, comprising 35 percent of individuals who use public Wi-Fi several times a month. Unsecured networks allow attackers to intercept data transfers.
- Mobile Ransomware: Holding personal data hostage, ransomware attacks constitute 30.8 percent of mobile threats.
- SQL Injection Attack: By injecting malicious SQL queries via input fields in apps, attackers have compromised mobile databases, exposing sensitive information and undermining data integrity across mobile platforms.
- Denial-of-Service (DoS) Attack: Around 80 percent of mobile e-commerce apps cyberattacks are prone to DoS assaults, overwhelming the network or service to render it unusable.
9. Data Breaches and Their Impact
Average Size of Data Breaches
The digital era has birthed an environment where vast amounts of data are constantly transferred and stored online, offering fertile ground for cybercriminals. And the size is trending upward.
- 2019: The year witnessed several significant breaches, but one of the largest was the exposure of nearly 885 million records from First American Financial Corp. The incident underscored the vulnerabilities even within esteemed financial institutions.
- 2020: Marriott International faced a second major data breach, compromising the data of approximately 5.2 million guests. It demonstrated organizations' enduring challenge in protecting customer data amidst increasingly sophisticated cyberattack techniques.
- 2021: By far, one of the most significant breaches was that of Facebook, where the personal data of over 530 million users was compromised, casting a spotlight on social media platforms' data security practices.
- 2022: Optus, one of Australia's largest telecommunications companies, suffered a breach impacting 9.8 million users, one of the most significant breaches in Australian history, underscoring the global nature of cyber threats.
- 2023: The trend has not abated in the past year, with substantial breaches impacting companies across various sectors, indicating that the risks are omnipresent and the potential for future breaches remains a critical concern.
The trajectory of data breach sizes points to an escalation in the number of records compromised per incident.
Differences in data sensitivity and value across sectors are stark:
- Healthcare: Holding the most sensitive personal data, healthcare breaches are particularly invasive. The 2021 breach of 3.5 million patient records at 20/20 Eye Care Network is a testament to the catastrophic potential when medical and personal data is compromised.
- Financial Services: This sector's breaches directly translate to fraud and identity theft. Last year's financial institution breach exposed millions to potential financial crimes.
- Retail: With a blend of personal and payment data, retail sector breaches, such as the 2020 Shopify incident affecting over 100 merchants, show the widespread dangers of data breaches.
- Government: Often underreported, government breaches can have profound implications for national security. The 2022 exposure of 500,000 sensitive records from a government database revealed the scope of information that can impact public trust and safety.
Consequences for Companies
The ramifications of data breaches extend far beyond the immediate aftermath.
- Reputation Damage: Companies like Yahoo, which experienced massive data breaches affecting billions of user accounts, have suffered long-lasting reputational harm.
- Financial Losses: According to IBM’s Cost of a Data Breach Report 2022, the average total cost of a data breach is $4.35 million.
- Legal Consequences: The GDPR and other data protection laws have led to hefty penalties for data breaches. For instance, British Airways faced a £183 million fine in 2019 for a breach affecting 500,000 customers.
- Stock Price Impact: Research from Comparitech has shown that stocks of breached companies can underperform in the market. For example, Equifax’s stock plummeted by over 30 percent following its 2017 breach.
- Customer Trust Issues: A breach can deeply erode trust, which takes years to rebuild. A survey by Ping Identity in 2020 revealed that 81 percent of consumers would stop engaging with a brand online after a breach.
- Regulatory Fines: The introduction of stringent regulatory standards, like GDPR in Europe, has seen companies like Google fined €50 million for breaches. These fines are not just financial penalties but also serve as a warning to others regarding data governance.
This detailed overview underscores the profound consequences that data breaches impose on companies in the short and long term and highlights the need for additional security measures.
10. Dark Web Activities
Sale of Stolen Data
The dark web has become an infamous digital bazaar where anonymity cloaks a nefarious exchange of contrabands and, most troublingly, stolen data. This underground market has shown both sophistication and alarming reach, reflecting broader trends in cybercrime.
- Personal Identifiable Information (PII): Complete identities, including names, social security numbers, and birth dates, are often bundled and sold. In the past year, a single bundle can fetch up to $1,000, depending on the data's freshness and comprehensiveness.
- Financial Data: Credit card details and bank account information are commodities traded daily. In the past year, the cybersecurity firm Cyble reported that the average price for stolen credit card data on the dark web was around $17-$120 per card.
- Medical Records: These records are highly valued for their sensitivity and the comprehensive personal information they contain. From 2009 to 2022, 5,150 healthcare data breaches involving 500 or more records were reported to the HHS Office for Civil Rights.
- Login Credentials: From streaming services to financial institutions, login credentials are sold en masse. A study by Digital Shadows highlighted over 15 billion stolen login pairs circulating in cybercriminal forums.
- Trade Secrets and Intellectual Property: The theft and sale of intellectual property and confidential business information can devastate innovation and competitiveness, with the Commission on the Theft of American Intellectual Property attributes an annual cost of $225 billion to $600 billion to China's alleged IP theft from the U.S.
Addressing the sale of stolen data on the dark web poses significant challenges for law enforcement due to anonymity technologies like Tor, jurisdictional hurdles, and the sophisticated tactics employed by cybercriminals to evade detection.
A Europol report on Internet Organised Crime Threat Assessment (IOCTA) emphasized the adaptability and resilience of dark web marketplaces despite law enforcement efforts. Consequently, this battle concerns technological capabilities, international cooperation, and legal frameworks that can keep pace with criminals.
Pricing Factors for Stolen Data
Many factors dictate the going rates for illicit information. Here is an analysis of the key elements influencing the price tags of the dark web's clandestine merchandise:
- Type of Data: Financial and medical records typically command higher prices than emails or login credentials due to the higher potential for fraud. A 2023 Dark Web Price Index report indicates credit card details can be priced up to $240, depending on the account balance.
- Freshness: Newly stolen data is more valuable because it's less likely to have been canceled or protected by identity theft services. The ‘Zero-Day’ market, where freshly obtained exploits are sold, can fetch thousands of dollars per record.
- Volume and Quality: Bulk discounts are standard; the more data offered, the lower the unit price. A single credit card number may sell for $5-$150, but in bulk, the price can drop to $1-$20 per number.
- Data Accuracy and Quality: Verified and detailed records are more expensive. Cybercriminals are willing to pay more for high-quality data.
- Source and Difficulty of Acquisition: Data from a reputable organization or high-profile breach can carry a premium price. For example, when LinkedIn experienced a data breach in 2021, the stolen data from 700 million users was particularly valuable due to the platform's standing.
These factors, combined, create a dynamic and fluctuating market on the dark web. Providing insights into this shadowy economy reflects an intricate picture of cybercrime and serves as a stark reminder of the importance of data security.
The Takeaway
As we digest the stark realities of the cybercrime landscape in 2024, the figures speak volumes. These are not just numbers but a clarion call to action, illuminating the need for increased cyber defenses.
Cybersecurity is no longer optional; it is imperative. Businesses and individuals must transform their approach to data protection. Vigilance, education, and robust security protocols are the pillars upon which we must build our digital resilience.
FAQ
What are the most common methods used to protect against cyberattacks in 2023?
Common defenses against cyber threats include advanced encryption, zero-trust security models enforcing strict access controls, and deploying AI-driven threat detection systems that continually learn from the cyber environment to thwart attacks preemptively.
How are governments responding to the rise in cybercrimes?
Governments worldwide are ramping up their response to cybercrime, enacting stricter regulations, forming dedicated cybersecurity task forces, and participating in international coalitions to combat cyber threats collaboratively. Investment in public cybersecurity infrastructure is also increasing to shield critical national services.
How long does it typically take for an organization to detect a cyber breach?
On average, organizations may take over 200 days to detect a cyber breach. This delay in response underscores the importance of investing in real-time monitoring tools and conducting regular security audits.
Are there any specific regions or countries that are more susceptible to cyberattacks?
Regions with less developed cybersecurity infrastructures, particularly in parts of Africa and Southeast Asia, often bear a disproportionate brunt of cyberattacks. These regions' growing digital economies present lucrative targets for cybercriminals exploiting inadequate security measures and lack of cyber awareness.
How do cybercriminals typically monetize the data they steal?
Cybercriminals typically monetize stolen data through direct sales on the dark web, ransom payments from data hostage scenarios, or more complex schemes like identity theft and financial fraud.