The dark web is a collection of websites and services intentionally hidden on privacy-focused overlay networks (most commonly Tor, short for The Onion Router) that aren’t indexed by mainstream search engines. To access these sites and networks, users will need specialized software like Tor Browser. Our guide will explain what the dark web is, how it works, what activities, legal and illicit, occur there, and how users can stay safe in 2025.
Key Takeaways: Dark Web in 2025
- The dark web is a set of websites and services intentionally hidden on privacy-focused overlay networks (Tor) that aren’t indexed by conventional search engines and require specialized software to access, like Tor Browser.
- It is a small slice of the overall internet but is heavily associated with anonymity and crime.
- The anonymity that the dark web provides is crucial for journalists, activists, and whistleblowers to bypass censorship, report abuses, and protect sources.
- Using the dark web in 2025 has significant risks, including exposure to cyber threats like malware and scams, encountering disturbing or illegal content, the potential for identity theft, and legal consequences.
What Is the Dark Web?
The dark web is a hidden set of websites and services on overlay networks that put privacy first. It is not indexed or accessible by mainstream browsers, like Chrome, Safari, and Firefox. Users need specialized software, like the Tor Browser, to access the dark web.
Unlike the everyday internet, it is designed for anonymity, obfuscating user identities, and their locations. Users access the dark web for a variety of reasons, but its inherent privacy and the anonymity it provides are part of its appeal. While many seek this veil of secrecy, it makes it difficult for authorities to monitor activity or track users.
The anonymity of the dark web offers legitimate protection for journalists and activists to communicate away from surveillance. However, this protection also provides safe haven for criminal activity and illicit transactions.
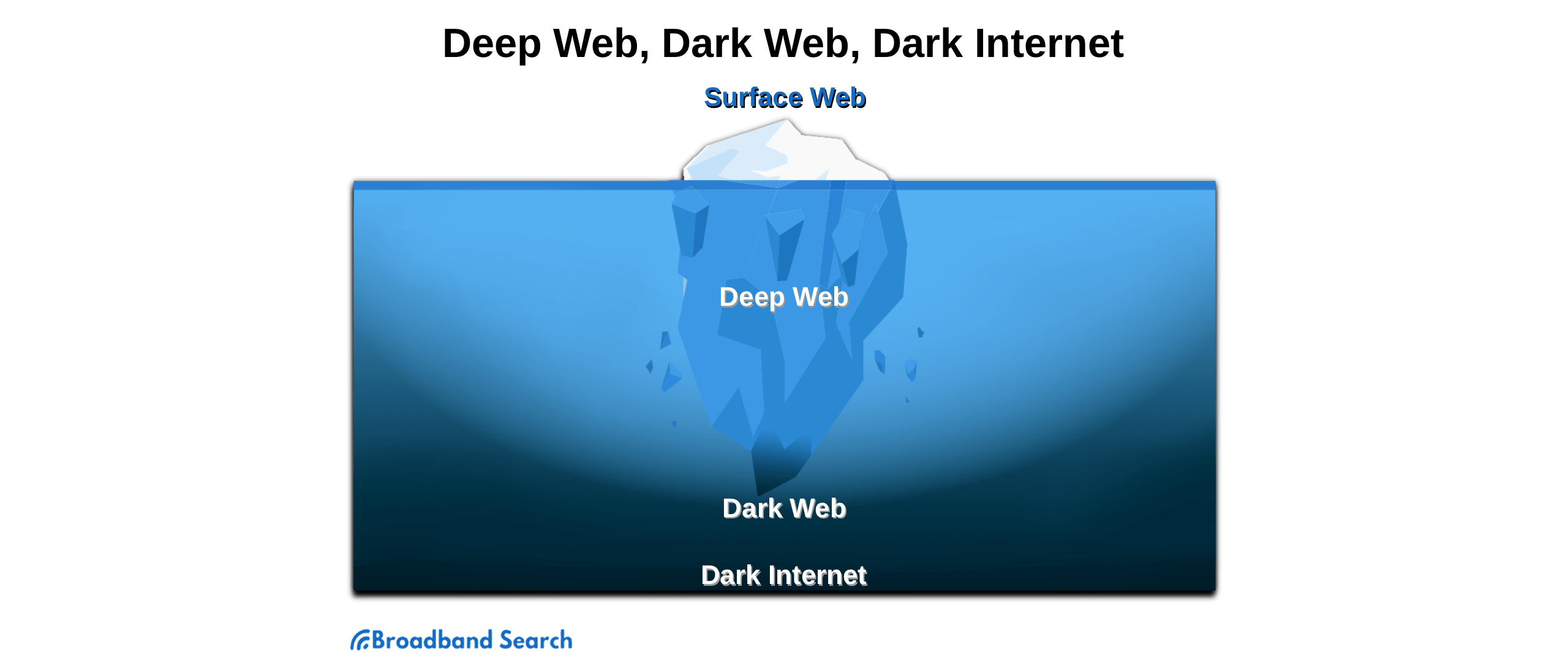
Dark Web vs Deep Web vs Surface Web
- Surface web: The surface web, or visible web, is the publicly accessible portion of the World Wide Web that's generally indexed by standard search engines like Google and Bing, including news sites, social media, online shopping, and government pages.
- Deep web: The deep web consists of pages behind logins, paywalls, or specific queries (e.g., email, banking, private intranets, cloud storage), making them inaccessible to standard search engines.
- Dark web: The dark web hosts onion services (“.onion” sites) that are accessible through the Tor network using software like Tor Browser. It's used for anonymous forums and messaging, and it can help people communicate privately and bypass censorship. But it doesn’t guarantee total protection from surveillance.
| Layer | What It Is | How You Access It | Typical Content | Indexed by search? |
|---|---|---|---|---|
| Surface web | Publicly visible internet pages | Standard web browsers (Chrome, Safari, Firefox) | News sites, social media, shopping sites, blogs | Yes, fully indexed by Google, Bing, etc. |
| Deep web | Hidden pages behind a barrier | Standard browser and valid login credentials or specific URL | Email accounts, banking, private databases, and medical records | No, generally private and protected data |
| Dark web | Intentionally hidden and encrypted layer | Specialized software like the Tor browser | Anonymous forums, secure communication | No, hidden explicitly from indexing |
Why Do People Use the Dark Web?
People use the dark web primarily for two reasons: to engage in illicit activities such as black markets and cybercrime, and to protect privacy for legitimate purposes like journalism, whistleblowing, and bypassing censorship.
- Illicit uses include black markets for illegal goods, trading stolen data, and coordinating cybercrime beyond law enforcement reach.
- Legitimate uses focus on privacy, serving journalists, whistleblowers, and citizens in repressive countries to bypass censorship and communicate securely.
Dark Web Drug Markets and Illegal Commerce
Modern dark web marketplaces mimic conventional e-commerce sites, featuring product listings, search functions, and user reviews.
Dark web marketplaces specialize in illicit goods like drugs, stolen data, fake documents, and malware. Merchants and sellers rely on anonymity to operate but are under pressure from international law enforcement agencies.
Law enforcement agencies worldwide have coordinated numerous high-profile operations, such as the takedowns of Silk Road, AlphaBay, Hydra, and Archetyp markets.
Child Exploitation and Other Abusive Content
Child sexual abuse material (CSAM) is the legal and ethical term for any medium, including images, videos, or live streams, that depicts the sexual exploitation or abuse of children.
The term "child pornography" is outdated and misleading, as it falsely suggests the content is a consensual act of pornography rather than an instance of serious abuse.
The term "CSAM" captures the harmful nature of the content and the real-life victimization involved, focusing on the act of abuse rather than the material itself. The dark web gives anonymity to entire communities of perpetrators to share CSAM.
A key focus for global law enforcement is dismantling the command structure and financial mechanisms that enable these organizations to operate across jurisdictions, thereby disrupting their capacity to harm citizens and economies worldwide.
Privacy, Censorship Resistance, and Whistleblowing
The dark web uses onion routing over the Tor network to provide anonymity and encryption. The technology facilitates secure, hard-to-trace communication for a variety of users.
Journalists and activists use the Tor browser to access censored information and communicate securely without revealing their location or identity. The browser encrypts traffic and routes it through a global network of volunteer relays, making it difficult to trace the origin and destination of communications.
Secure leak platforms like SecureDrop and GlobaLeaks operate as dark web services, allowing whistleblowers to submit sensitive materials anonymously.
Intelligence agencies (e.g., MI6's "Silent Courier") also use the dark web for secure contact portal, illustrating the technology's dual-use nature.
Is It Legal to Use the Dark Web?
Accessing the dark web itself is generally legal in many countries, including the U.S., because tools like Tor are designed for privacy. However, certain activities on the dark web are serious crimes. Here are examples of actions that cross the legal line:
- Illicit Drug Trafficking or Distribution
- Illegal Firearms Trafficking
- Production or Distribution of Child Sexual Abuse Material (CSAM)
- Hiring Hackers and Solicitation for Cybercrime
- Buying and Selling Stolen Data
Be aware that law enforcement agencies around the world monitor, investigate, and frequently infiltrate illegal online markets and dark web forums to track down perpetrators of these crimes.
Do I Need the Dark Web?
For most people, no. If your goal is everyday privacy (safer browsing, fewer trackers, protected public Wi-Fi, or better account security) you can usually get what you need with strong passwords, MFA, reputable security software, and privacy tools on the regular web (like encrypted messaging apps and privacy-focused browsers).
When Tor or the dark web might make sense
You may have a legitimate reason to use Tor (and possibly access onion services) if you:
- Live in or are traveling through a place with heavy censorship or blocked news sites
- Need to protect your identity while researching sensitive topics (journalism, activism, whistleblowing)
- Want to access privacy-focused services that intentionally operate as onion sites (like secure tip lines)
When you should not use it
Avoid the dark web if you:
- Just want “more privacy” in general when tools exist with better results
- Plan to log into banking, work, or primary email accounts
- Aren’t prepared for higher exposure to scams, malware, and illegal and disturbing content
- Think “Tor makes me anonymous” (it reduces tracking, but doesn’t guarantee anonymity)
Better alternatives for most people
If your goal is privacy, not dark web browsing, start here instead:
- Encrypted messaging: Signal for private communication
- Secure drop and tip tools: SecureDrop (for whistleblowing)
- Everyday security: password manager, MFA, updated OS and browser
- Public Wi-Fi safety: use a reputable VPN and avoid sensitive logins on unknown networks
Bottom line: If you don’t have a clear, legitimate reason, such as censorship resistance or source protection, you probably don’t need the dark web. Focus instead on security hygiene and privacy tools that carry less risk.
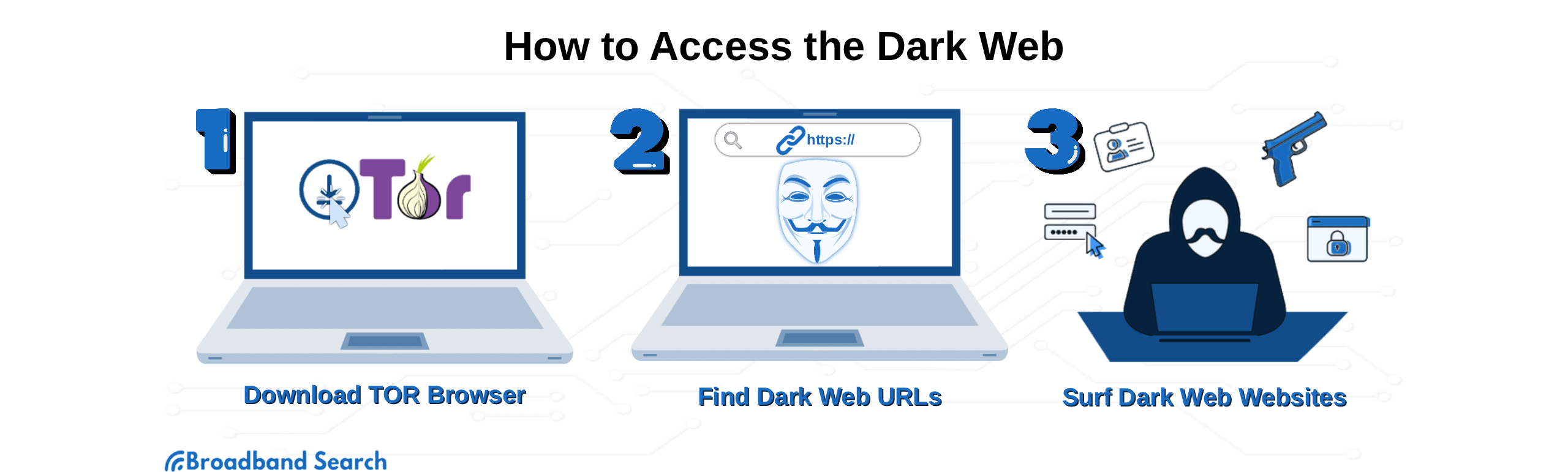
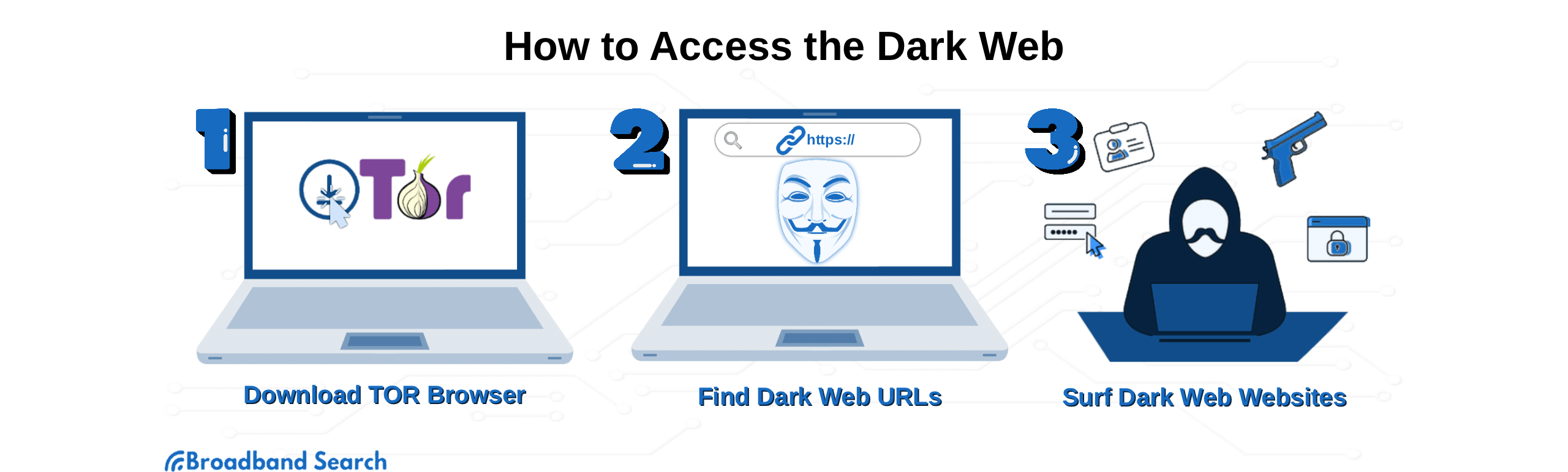
How to Access the Dark Web (Safely)
Now that you understand the nature and legal aspects of the Dark Web, you might be curious about how to access it. Rather than providing a roadmap to the dark web, we’re going to focus on safety while using it.
While gaining entry is relatively straightforward using specialized software like the Tor Browser, actively participating in its communities and activities often requires specific knowledge and connections.
A word of caution first. Once on the dark web, you’ll be in unregulated territory. Any link you click or path you follow can trigger malware deployment, illicit content, or privacy breaches. Do some research before launching Tor Browser. Have a clear purpose and know how to do it as safely as possible.
Proceed with caution and at your own risk.
Tor Browser (must-have for access)
To access the dark web, you first need the Tor Browser. This specialized browser is essential because it provides the encryption layers required to maintain your anonymity and obscure both your identity and the source of the information you access.
Accessing the dark web carries significant risks, including exposure to illegal content and potential security threats. Engaging with such content can have severe legal and personal consequences.
VPN: Extra Privacy Layer
While the Tor browser offers anonymity, users seeking maximum privacy often add a Virtual Private Network (VPN) for extra security.
The VPN encrypts your traffic before it hits the Tor network, hiding your Tor usage from your ISP and further obscuring your online presence.
- Prevents your ISP from knowing you are accessing the Tor network.
- The Tor network sees the VPN's IP address, not your actual location.
- Encrypts all other internet activity on your device.
VPNs are for privacy and security only. Using a VPN with Tor does not negate illegal activity.
Security Software and Safe Devices
Here are key practices for maintaining security software and using devices safely:
- Keep your operating system (OS) and applications up to date.
- Install and regularly update antivirus (AV) and anti-malware software.
- Be cautious about all software sources.
- Consider using a VM (virtual machine) or a device that is only used to access the dark web and has minimal private information associated with it.
Password Managers and Strong Authentication
Stolen credentials on the dark web pose a significant risk, allowing attackers to steal identities and access multiple accounts.
Strong passwords and Multi-Factor Authentication (MFA) are your best defense.
- Use a password manager to create and store unique, strong passwords for all accounts.
- Enable MFA/2FA everywhere for an essential second layer of security, even if a password is stolen.
Dark Web Monitoring & Breach Alerts
Instead of checking dangerous sites yourself, use monitoring services to watch for your data:
- Identity theft protection services scan underground markets for your personal information (email addresses, credit card numbers, etc.).
- Alerts notify you immediately if your data is found in a breach so that you can change passwords quickly.
- Free tools like haveibeenpwned.com also offer alerts to check if your email was in a data breach.
Why Dark Web Browsing Is Slow and Unstable
Dark web browsing is intentionally slow and unstable due to the technology designed to protect user anonymity.
The network achieves its security through multi-hop routing (data is bounced through several volunteer relays worldwide) with heavy encryption at each step. It means that your data travels a much longer, more complicated path to its destination than standard internet traffic, resulting in slower speeds and frequent connection issues.
For those interested in how to access the dark web safely, these speed limitations are a necessary trade-off for enhanced privacy.
Dark Web Facts and Statistics (2025 Snapshot)
Here are a few dark web facts and statistics that help put things in perspective in 2025.
- The dark web makes up a very small portion of the total internet content (only about 0.01%).
- The Tor Browser, the primary browser used to access the dark web, has seen its daily user base grow to over 3 million by early 2025.
- While a significant amount of content is illegal (around 57% in an older study), 6.7% of Tor users likely use it for malicious purposes on an average day; many use it for privacy or journalistic purposes.
- The illicit dark web economy generates significant revenue, estimated at around $1.5 billion annually from stolen data and goods.
- Law enforcement has conducted successful global operations; for example, Operation RapTor in May 2025 resulted in 270 arrests and the seizure of over $200 million in currency and cryptocurrency, yet marketplaces often re-emerge quickly.
- By 2022, more than 15 billion account credentials were found circulating on dark web forums, highlighting the immense volume of compromised data available.
The Dark Web in the News and Law Enforcement Crackdowns
Global law enforcement agencies are increasingly successful at infiltrating and dismantling illicit marketplaces and networks. Recent international crackdowns leverage intelligence, blockchain analysis, and coordinated operations to identify and prosecute criminals.
Ongoing efforts by law enforcement around the world demonstrate that no one is beyond the reach of the law, even in the hidden corners of the internet.
Dark Web Market Takedowns
Dark web marketplaces are consistently targeted and dismantled by global law enforcement operations, proving there are no safe havens in the hidden corners of the internet.
- The original Silk Road was the first major dark web market, operating from 2011 until the FBI shut it down in October 2013.
- Subsequent copycat sites like Silk Road 2.0 and AlphaBay quickly emerged, only to be dismantled by coordinated international operations, such as Operation Bayonet in 2017.
- In June 2025, a Europe-wide operation, led by German authorities with support from Europol and U.S. agencies, took down Archetyp Market, the longest-running dark web drug market, effectively cutting off a central supply line and reinforcing the message that even sophisticated markets are vulnerable to detection and closure.
Cybercrime and Data Breaches
Dark web forums serve as hubs for cybercriminal activity due to their anonymity, facilitating the exchange of stolen data, malware, and attack tools.
Recent statistics indicate an increase in data breaches and ransomware attacks originating from these underground forums.
Bitcoin, Cryptocurrencies, and Dark Web Payments
Pseudonymous cryptocurrencies such as Bitcoin are advantageous to dark web marketplaces because they enable global transactions that are more difficult to track than standard bank transfers.
Cryptocurrency transactions are not entirely anonymous, as blockchain analytics firms and law enforcement have developed advanced techniques to trace funds and identify individuals.
How the Dark Web Is Changing in 2025
The dark web in 2025 is an evolving, increasingly professionalized ecosystem marked by several key trends.
- More fragmentation and specialization: The landscape is shifting toward smaller, more resilient groups that operate in private, invite-only communities or leverage encrypted messaging apps like Telegram to evade law enforcement.
- Growing role of state-sponsored and organized cybercrime: Organized cybercrime groups have adopted business-like models, including "as-a-service" offerings for ransomware and malware, which lowers the barrier to entry for new attackers.
- Ongoing debate over privacy tools vs. abuse: There is a persistent ethical and legal debate over the use of privacy-enhancing tools such as the Tor network and cryptocurrency mixers. While essential for journalists, activists, and whistleblowers, these tools are also exploited by criminals.
How to Protect Yourself from Dark Web Risks
To protect yourself from the dangers of the dark web and minimize risk from potential data breaches, follow these actionable steps:
- Secure your credentials: Use strong, unique passwords for every online account and store them using a reputable password manager.
- Enable multi-factor authentication (MFA): Turn on MFA on all critical accounts, especially email, banking, and social media, to add an essential layer of security.
- Monitor for breaches: Stay vigilant for data-breach notifications from companies you interact with. Consider subscribing to a dark web monitoring service offered by your bank, credit card issuer, or a dedicated security provider to receive alerts if your information is found online.
- Limit personal data sharing: Be highly selective about the personal data you share with apps, AI tools, and websites, as any data collected could eventually end up on the dark web if the service is compromised.
- Act quickly after a breach: If a major company that holds your data is breached, immediately consider placing a credit freeze or fraud alert with the major credit bureaus to prevent identity theft.
FAQ
What is the dark web, and how is it different from the deep web?
The deep web includes non-indexed internet content you use daily, like email and banking sites, accessible via a URL and login.
The dark web is a small, hidden part of the deep web requiring specific software, like the Tor Browser, for maximum anonymity. While known for illegal activities, it also provides essential privacy tools for journalists and activists.
Is going on the dark web legal?
Accessing the dark web is not illegal in most countries, including the United States, as it can be used for legitimate purposes such as anonymous communication and accessing uncensored news. The software used to access it, like the Tor Browser, is legal to download and use.
The crucial distinction lies in the activities conducted while on the dark web. Engaging in illegal acts there, such as buying or selling drugs, weapons, stolen data, or CSAM, is a serious crime and subject to severe legal penalties.
What actually happens on the dark web?
The dark web hosts a mix of legal and illegal activities, including anonymous communication, the sale of illicit goods like drugs and weapons, and forums for privacy-focused discussions.
When was the dark web created?
The origins of the dark web date back to the mid-1990s, when the U.S. Naval Research Laboratory developed "onion routing" technology. The first software to enable dark web functionality was Freenet, released in March 2000.
How can I tell if my personal data is on the dark web?
You can determine if your personal data is on the dark web using free data breach checker websites or by signing up for a dedicated dark web monitoring service.
How big is the dark web today?
The dark web is a tiny portion of the internet, though total size is difficult to quantify, yet it hosts a significant volume of activity and data.
Who made the dark web?
The U.S. Naval Research Laboratory developed "onion routing" technology in the 1990s.
What the Dark Web Really Means for You in 2025
The dark web functions primarily as an anonymity tool used for both legitimate privacy and widespread criminal activities in 2025.
While law enforcement targets illicit operations, criminals adapt, maintaining the network's high-risk environment.
- Most users do not need to access it for personal safety or privacy needs.
- Prioritize strong security hygiene: Implement robust password management, enable multi-factor authentication (MFA), and be cautious about sharing personal data online.
- A cat-and-mouse game continues: Law enforcement agencies actively pursue and shut down criminal enterprises, but operators quickly adapt and move their illegal activities.