In our increasingly online lives, cybersecurity isn't just an IT issue—it's your issue. A staggering 3.5 million cybersecurity jobs are unfilled globally, reflecting its soaring demand. Why? Simple: hackers don't sleep. They constantly evolve, making yesterday's safety measures obsolete today.
Globally, cybersecurity landscapes vary dramatically. Countries like Australia and the Netherlands lead in safeguarding digital spaces, while others lag, exposing businesses and individuals to greater risks. Let’s take a look at some of these differences and outstanding performers.
Understanding Cybersecurity Metrics
When assessing a country's cybersecurity strength, specific metrics offer a clear picture:
Number of Cyber Attacks
Cyber threats are escalating globally, with a 600 percent rise in cyberattacks since the pandemic began. In 2021 alone, there was a 102 percent surge in cybercrime involving ransomware compared to the beginning of 2020. The global cost of cybercrime is projected to reach $10.5 trillion annually by 2025.
National Cybersecurity Policies
Governments worldwide are intensifying their focus on cybersecurity. The UK, following the lead of the US, is strengthening its Network and Information Systems (NIS) Regulations. Other nations like Australia, Germany, and Japan are also adopting similar policies. Organizations such as NIST and WEF are issuing advisories to enhance cyber resilience, particularly in critical infrastructure and healthcare.
Public Awareness and Education
The global security awareness training market is booming and is expected to exceed $10 billion annually by 2027. This growth, up from around $5.6 billion in 2023, indicates a rising emphasis on cybersecurity knowledge and skills among the public and professionals. Countries that invest more in awareness and education are better prepared and generally more secure.
Technological Infrastructure and Investment
Investments in cybersecurity are rising, with global spending expected to grow by 13.2 percent in 2023, reaching approximately $223.8 billion. This growth is driven by the persistent threat of cyberattacks, emphasizing the critical need for robust technological infrastructure and proactive investment in cybersecurity measures.
The Best Countries for Cybersecurity
Identifying the best countries for cybersecurity involves scrutinizing government initiatives, technological infrastructure, incident response capabilities, and public awareness levels. These criteria reveal a clear divide: nations excelling in these areas provide robust digital safety nets, setting benchmarks in global cyber defense.
Here are some of the top performers.
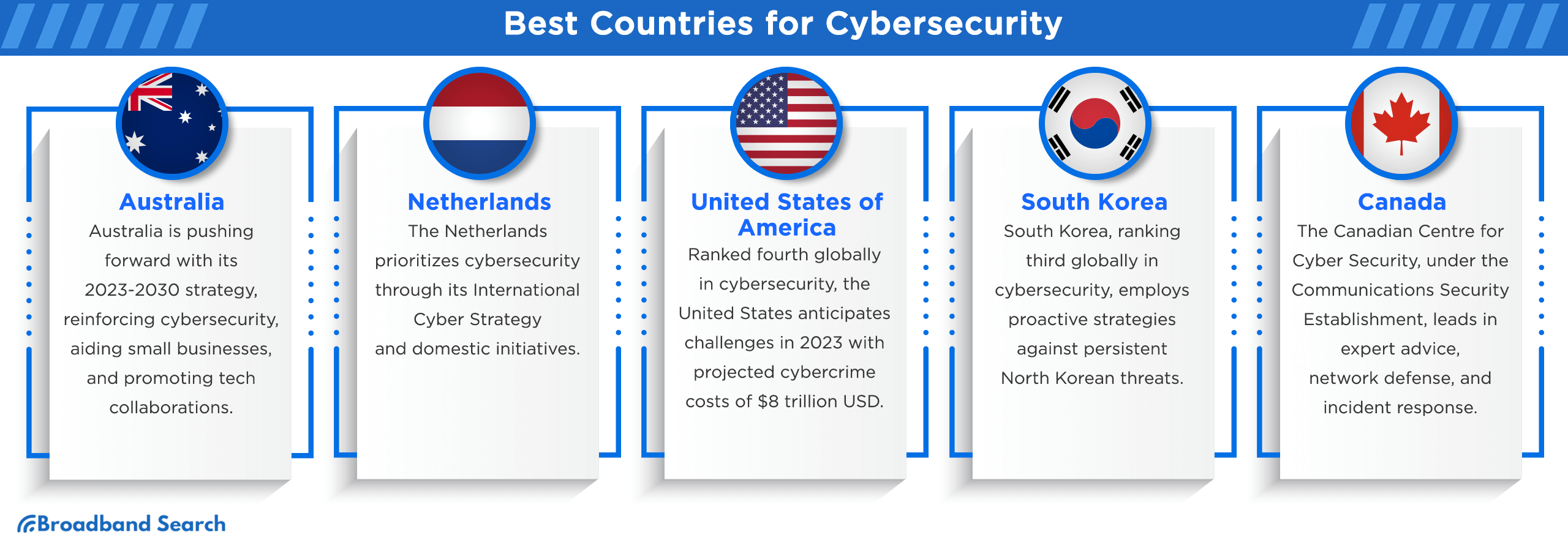
Australia
Australia ranks impressively in global cybersecurity, per the Cyber Defense Index 2022/23 (it has the top spot).
Government-Led Cybersecurity Initiatives
The Australian Government, under its 2023-2030 Cyber Security Strategy, aims to establish Australia as a world leader in cybersecurity by 2030. This comprehensive strategy includes forming a cyber security assistance team to bolster resilience in the Pacific region. Notably, the strategy encompasses support for small and medium businesses, recognizing their vulnerability to cyber incidents.
Technological Infrastructure and Public Awareness
Australia's commitment to cybersecurity is further evidenced through groundbreaking collaborations, like that between the Tide Foundation and RMIT University. This partnership has led to significant advancements, such as 'ineffable cryptography,' a technology enhancing critical infrastructure security like ports and energy grids. Such innovations play a crucial role in mitigating the impact of 143 cyber attacks recorded in the past year, marking a substantial rise from the 95 incidents reported in the preceding year.
Incident Response Capabilities
To enhance incident response capabilities, the Australian government conducts cyber war games with critical infrastructure firms. These exercises, involving key sectors like finance and aviation, are designed to test and improve responses to severe cyber attacks. Additionally, the government collaborates with major finance companies to simulate responses to cyber attacks on essential services like banking, focusing on rapid recovery and maintaining functional systems during crises.
Netherlands
The Netherlands, renowned for its digital advancement, is committed to a digitally secure nation. Its cybersecurity strategy is designed to capitalize safely on digitalization's economic and social opportunities while safeguarding security and public values. The country's digital systems, likened to a society's central nervous system, present both opportunities and risks.
Government Cybersecurity Policies
The Netherlands' International Cyber Strategy 2023-2028 articulates its goal of contributing to a secure, open, and free cyber domain. This strategy is driven by the Ministry of Foreign Affairs, with a dedicated cyber ambassador reinforcing the nation's commitment to internet safety. Additionally, the Dutch government’s Netherlands Cybersecurity Strategy focuses on achieving a digitally secure Netherlands, enhancing both economic and social opportunities through digitalization.
Technological Infrastructure and Public Awareness
The Netherlands boasts an advanced technological infrastructure, making it an ideal hub for cybersecurity events and innovation. This environment fosters a vibrant tech industry and a multicultural ecosystem where experts and enthusiasts converge to share knowledge and explore cybersecurity trends. Such a setting bolsters technological defenses and cultivates public awareness and engagement in digital security matters.
Incident Response Strategies
In response to the evolving digital threat landscape, the Netherlands emphasizes adaptability in security. The Cyber Security Assessment Netherlands 2023, published by the National Coordinator for Counterterrorism and Security in cooperation with the National Cybersecurity Centre, calls for organizations to expect the unexpected and adapt their security accordingly.
This assessment acknowledges the complexity of cyber threats, including state-sponsored cyberattacks and cybercriminal activities such as extortion and data theft. The focus is on enhancing resilience, reducing the impact of incidents, and limiting damage, thereby addressing the imbalance between digital threats and national cybersecurity resilience.
United States of America
Ranked fourth globally in the Cyber Defense Index 2022/23, the United States stands out in cybersecurity.
In 2023, cybersecurity remains a significant challenge, with global cybercrime costs expected to reach $8 trillion USD. The U.S. employs over 1.1 million cybersecurity professionals. Yet given the United States’ status as a technology leader, this still is not enough, and further improvements are always necessary.
Federal and State-level Cybersecurity Policies
The Biden-Harris Administration released the National Cybersecurity Strategy in 2023, focusing on securing critical infrastructure and fostering international cooperation against digital threats. Complementing the 2022 National Security Strategy, this strategy is a cornerstone in operationalizing cybersecurity priorities at both federal and state levels.
Technological Advancements and Infrastructure
The U.S. cybersecurity landscape in 2023 is defined by evolving threats and technological advancements. Adopting hybrid and multi-cloud security approaches is prominent, addressing the nuanced needs of businesses while ensuring data protection and security. Moreover, the U.S. is keenly aware of the threats posed by Advanced Persistent Threats (APTs) and is actively working to mitigate these risks. The advancement towards post-quantum cryptography also highlights the U.S.'s proactive stance in securing its digital infrastructure against emerging quantum computing threats.
Public Awareness and Incident Response Mechanisms
The Biden-Harris Administration's National Cybersecurity Strategy Implementation Plan emphasizes a whole-of-government approach, coordinating initiatives across various federal agencies for a resilient, equitable, and defensible cyberspace. The National Cyber Incident Response Plan update by the Cybersecurity and Infrastructure Security Agency (CISA) is critical in ensuring coordinated government action and clear guidance to external partners during cyber incidents.
South Korea
South Korea ranks third in the Cyber Defense Index 2022/23 by MIT Technology Review, excelling in policy commitment and critical infrastructure. This achievement is significant given the persistent cyber threats from North Korea, including a significant cryptocurrency theft by the Lazarus Group in 2021, impacting many South Koreans.
Government Initiatives for Cybersecurity
South Korea has established a proactive and offensive cybersecurity strategy, aimed at countering sophisticated cyber threats. This strategy involves ramping up cyberwarfare capabilities, a necessity in the face of escalating cyber threats to the military and defense industry.
Furthermore, Seoul maintains a cybersecurity guidance agreement with the US to facilitate smooth joint cyber military operations, emphasizing the importance of international cooperation in this domain. These initiatives respond to threats like North Korean hacking activities targeting weapons development programs and personal information for cyber espionage.
Technological Infrastructure and Public Awareness Measures
The South Korean cybersecurity market is projected to grow significantly, from USD 3.83 billion in 2023 to USD 7.70 billion by 2028. This growth is fueled by the increasing number of connected devices and advanced use of mobile devices, making the country a prime target for cyber-attacks. In response, the government invests heavily in cybersecurity capabilities, as indicated by its high ranking in the International Telecommunication Union Global Cybersecurity Index.
The country is also actively developing infrastructure to respond to cybersecurity threats in real-time, in collaboration with central cloud and data center companies. Additionally, South Korea's involvement in international cybersecurity efforts, like joining NATO's Cooperative Cyber Defense Centre of Excellence, further reinforces its commitment to enhancing cybersecurity measures.
Incident Response Strategies and Their Effectiveness
South Korea's incident response strategy is exemplified by the establishment of the Cyber Threat Analysis & Sharing (C-TAS) system by KISA, which shares a wide range of cyber threat information across industries. The Cyber Breach Response Headquarters, also established by KISA, plays a pivotal role in monitoring, responding to, and preventing the recurrence of breach incidents.
Canada
Canada's prominence in cybersecurity is no accident. The Index evaluates major economies on cybersecurity assets, organizational capabilities, and policy frameworks. Canada's high ranking reflects its robust adoption of better technology practices and governmental policies promoting secure digital transactions.
Cybersecurity Policies and Government Initiatives
The Canadian Centre for Cyber Security, part of the Communications Security Establishment, stands as Canada's technical authority on cybersecurity. This Centre offers expert advice and services and ensures cooperation with various sectors to strengthen cybersecurity across the nation. Their work includes offering tailored cybersecurity advice, defending government networks with sophisticated tools, and leading operational responses during cyber events. This cohesive approach underscores the Centre's commitment to enhancing Canada's cybersecurity resilience in the face of evolving technological threats.
Infrastructure and Public Engagement in Cybersecurity
Canada's cyber threat landscape continuously evolves, with threats employing artificial intelligence and other innovative techniques. A PwC Canada report highlights this dynamic environment, driven by geopolitical tensions and rapid digitization. In response, Canadian organizations increasingly prioritize cybersecurity in their resilience plans, with many executives considering cybercrime as their most significant threat.
The trends for the coming years include AI reshaping the cyber threat landscape, a surge in sophisticated ransomware attacks, and heightened threats to data security and critical infrastructure.
Incident Response Capabilities
The Government of Canada has prioritized cybersecurity, evident in the passage of the CSE Act and significant investments, including $875.2 million to enhance the Communications Security Establishment's ability to counter cyber threats. This move is geared toward protecting critical infrastructure, government systems, and national security.
Additionally, the Cyber Centre works closely with businesses and organizations affected by cyber incidents to mitigate their impact and strengthen overall cybersecurity resilience.
The Worst Countries for Cybersecurity
Countries with poor cybersecurity often share alarming traits: underdeveloped digital infrastructure, inadequate policies, and a high incidence of cybercrime. These factors compromise national security and hinder economic growth and public confidence.
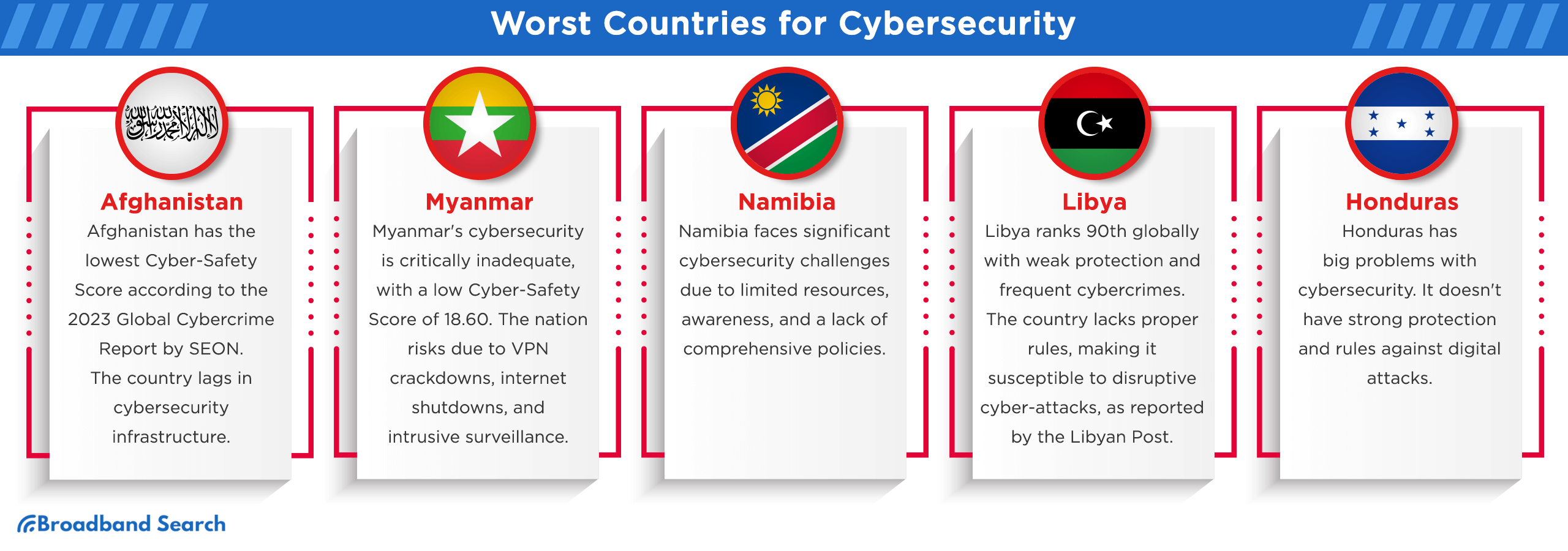
Afghanistan
According to the 2023 Global Cybercrime Report by SEON, Afghanistan has the lowest overall Cyber-Safety Score.
Lack of Robust Cybersecurity Infrastructure
Afghanistan, unfortunately, lags significantly in cybersecurity infrastructure. Until 2001, Afghanistan had no information and communications technology institutions or Internet service providers. This absence hindered the development of a strong cybersecurity infrastructure.
Although the Ministry of Communications and Information Technology developed ICT policies from 2003 onwards, comprehensive legislation, including a Cyber Crime Law and a Cyber Security Policy, has faced delays and complexities.
High Vulnerability to Cybercrime
This susceptibility is further exemplified by specific incidents, such as the advanced persistent threat (APT) attack targeting an Afghan government entity using a previously undocumented web shell called HrServ.
Cyber-Safety Score: 5.63
To put these concerns into perspective, Afghanistan's Cyber-Safety Score stands at a precarious 5.63. There is practically nowhere to go but up.
Myanmar
Myanmar emerges as a critical case in cybersecurity vulnerabilities. The country's cybersecurity measures are severely inadequate, often marred by a weak legal framework. Its cyber-safety score of 18.60, alarmingly low, reflects significant risks for businesses and individuals operating within or interacting with entities in Myanmar.
Inadequate Cybersecurity Measures
The crackdown on VPNs in Myanmar, essential for anonymizing a user's Internet Protocol address and bypassing firewalls, represents a significant attack on digital rights. This is compounded by extensive internet shutdowns and surveillance activities since the military coup on February 1, 2021. Additionally, telecom and internet service providers were secretly ordered to install intercept technology to enable the army to eavesdrop on citizen communications, as revealed by a Reuters investigation.
Weak Legal Framework
Myanmar's legal framework for cybersecurity needs substantial improvement to align with international standards. The current draft of the cybersecurity law would grant sweeping powers to the authorities, such as accessing user data, blocking websites, ordering internet shutdowns, and prosecuting critics. This law would also apply to a broad range of digital platform services, extending beyond social media to include financial services and data processing services.
Cyber-Safety Score: 18.60
Myanmar has a Cyber-Safety Score of 18.60, among the lowest globally. The score highlights the country's inadequate response to cyber threats and the lack of comprehensive strategies to safeguard against digital risks.
Namibia
Namibia, while a land of stunning landscapes, faces cybersecurity challenges due to limited resources, cybersecurity awareness, and a lack of comprehensive policies. Its vulnerability exposes individuals and organizations to cyber threats, emphasizing the importance of strengthening defenses and promoting cybersecurity education to mitigate risks effectively.
Poor Cybersecurity Infrastructure
Namibia's cybersecurity measures are notably weak. Elton Witbooi, an executive at the Communications Regulatory Authority of Namibia, highlighted the country's vulnerabilities in cybersecurity, citing shortcomings in law, technology, organization, capacity development, and cooperation. The absence of a comprehensive legal framework governing cybersecurity further exacerbates these issues
High Risk of Cyber Crimes
Namibia has seen a significant increase in cybercrimes. In 2022, the country experienced a 40 percent surge in reported cyberattacks. This rise in cyber threats includes phishing, malware, and data breaches. With a small population, the number of cyber-attacks recorded – 2.7 million in 2022 – is alarmingly high for the country's size.
Cyber-Safety Score: 19.72
Namibia's Cyber-Safety Score, at a mere 19.72, ranks among the lowest in the world. This low score results from the country's inadequate efforts in combating cyber threats and its deficiency in implementing solid strategies to safeguard its digital environments.
Libya
Libya's cybersecurity situation is precarious, marked by inadequate measures and a high prevalence of cybercrimes. Here's an analysis:
Analysis of Cybersecurity Measures and Policies
Libya is significantly vulnerable to cybersecurity threats, ranking 90th globally. This vulnerability stems from inadequate safeguards against cybercrimes and weak or non-existent cybersecurity legislation, leaving sensitive transactions at risk. These shortcomings make Libya highly susceptible to cyber-attacks.
Assessment of Cybercrime Prevalence
Libya has been experiencing relentless cyber-attacks, as reported by the Libyan Post, Telecommunication and Information Technology Holding Company (LPTIC). These attacks have disrupted services.
Honduras
Honduras faces significant challenges in cybersecurity, marked by underdeveloped infrastructure, a nascent legal framework, and escalating cybercrime rates.
Overview of Cybersecurity Infrastructure
Honduras has limited capacity to combat cybersecurity threats. Its underdeveloped cybersecurity infrastructure reflects a lack of robust systems and measures to protect against digital attacks. This situation leaves the country vulnerable to a range of cyber threats.
Evaluation of Legal Framework and Cybercrime Rates
Despite new legislation in 2019 addressing cybercrime, Honduras still lacks specific measures for electronic evidence, rendering the legal framework inadequate for effectively combating cybercrime. In the first six months of 2021, the Honduran Secretariat of Defense reported that the FNAMP (National Anti-Maras and Gangs Force) prevented extortion payments amounting to approximately $400,000. This statistic highlights the prevalence of extortion-related cybercrimes in the country.
Cybersecurity Challenges and Future Trends
Cybersecurity challenges have transcended national boundaries, evolving into a global concern that affects individuals, businesses, and governments worldwide. The rapid digitization of critical infrastructure, from energy grids to healthcare systems, has made these sectors susceptible to cyberattacks that can disrupt daily life and even jeopardize national security.
Furthermore, it's crucial to acknowledge that cybercrime operates on an international scale. Cybercriminals often target individuals and organizations outside their home countries, rendering law enforcement and attribution more challenging. These criminals frequently work collaboratively, forming collectives or participating in organized crime networks, further complicating the fight against cyber threats.
The Globalization of Cybersecurity Threats
The evolution of cybersecurity threats has led to a globalized landscape where attacks can originate from anywhere and target anyone. Recent statistics reveal that cyber threats have surged in both scale and sophistication, with a substantial increase in ransomware incidents worldwide. These attacks transcend borders, highlighting the urgency for international cooperation in combating this shared threat.
Impact of the Digitization of Critical Infrastructure
The digitization of critical infrastructure has far-reaching consequences for national security and our everyday routines. Here are the top five impacts:
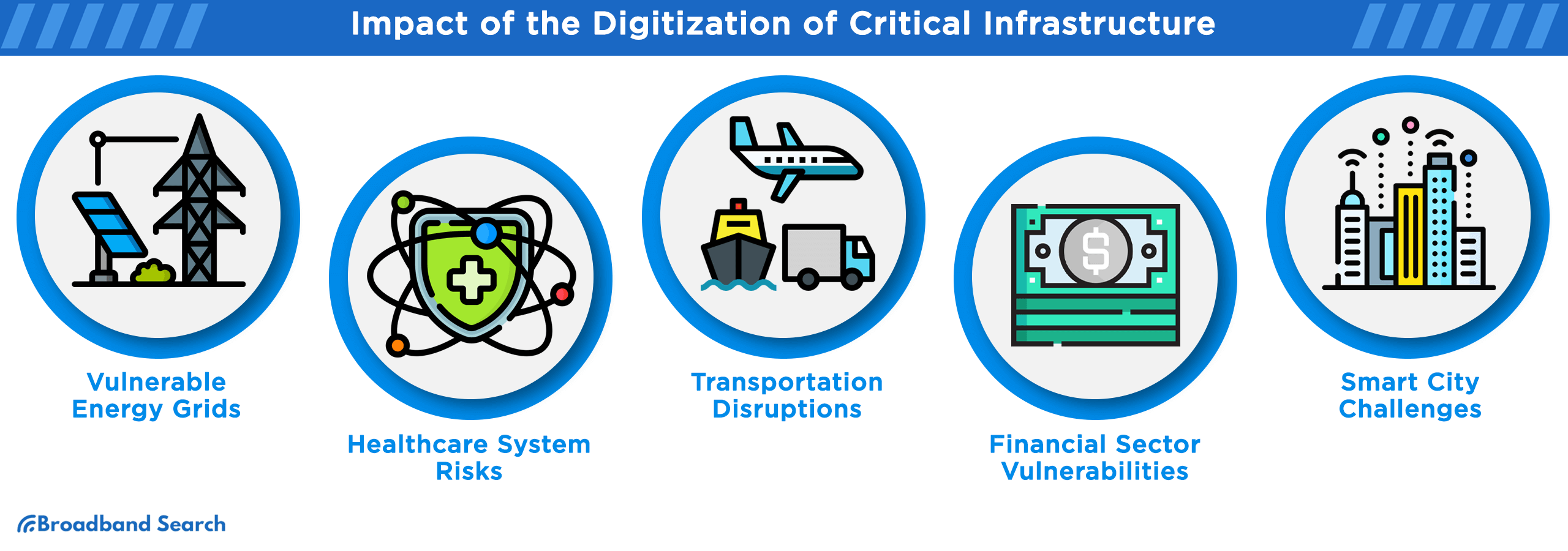
- Vulnerable Energy Grids: Digitized energy grids are susceptible to cyberattacks that can disrupt power supply, impacting homes and businesses.
- Healthcare System Risks: Healthcare institutions, reliant on digital records and devices, face threats that can compromise patient data and even disrupt medical services.
- Transportation Disruptions: Cyberattacks on transportation systems can lead to logistical chaos, affecting the movement of goods and people.
- Financial Sector Vulnerabilities: The financial industry's digital transformation makes it a prime target, endangering economic stability.
- Smart City Challenges: Cities embracing smart technologies risk disruption in services crucial to urban life, from public transportation to waste management.
The International and Collective Nature of Cybercrime
Cybercriminals often target victims outside their home countries, exploiting the interconnectedness of digital networks. This global reach is demonstrated by the fact that nearly 1 billion emails were exposed in a single year, affecting 1 in 5 internet users globally. Additionally, during Russia's invasion of Ukraine, Russian-based phishing attacks against European and US-based businesses increased 8-fold.
Examples of Significant International Cyber Attacks
- Indian Hacktivists vs. Canada (September 2023): Indian hacktivists launched DDoS attacks on Canada’s military and Parliament websites. The motivation was linked to Canadian Prime Minister Justin Trudeau's accusations against India
- Iranian Attack on Israel's Railroad Network (September 2023): Iranian hackers targeted Israel’s railroad infrastructure using phishing techniques. Brazilian and UAE companies were also targeted in this multifaceted attack.
- Chinese Hackers Targeting US and Japan (September 2023): Chinese state-sponsored hackers allegedly infiltrated routers in the US and Japan, targeting government and industrial sectors with firmware implants.
- Cyberattack on Bermuda’s Government Services (September 2023): Bermuda’s Department of Planning and other government services experienced a massive cyberattack, causing disruptions for several weeks.
- Phishing Ransomware Attack in Kuwait (September 2023): Kuwait’s Ministry of Finance was targeted by a phishing ransomware attack. The government took immediate steps to isolate its systems to prevent further attacks.
Challenges in Enforcement
Enforcing laws across international borders presents several challenges. Key difficulties identified by the Departments of State, Justice, and Homeland Security, along with international experts, include a lack of dedicated resources, difficulties in retaining highly trained staff, and inconsistent definitions of “cybercrime”. The scale of the problem is significant: in 2021, the FBI received over 840,000 cybercrime complaints, with losses exceeding $6.9 billion
Examples of International Cooperation and Failures in Cybercrime Enforcement
- 16Shop Phishing Platform Takedown: A global effort led by INTERPOL, involving the United States, Indonesia, Japan, and other partners, dismantled the '16Shop' phishing platform, which affected 70,000 users in 43 countries.
- UN Cybercrime Convention Challenges: The ongoing negotiations for the UN CybercrimeConvention in New York City reflect the complexities of international cooperation in law enforcement. Ambiguities and broad provisions in the convention could inadvertently compromise human rights and privacy, illustrating the challenges in reaching a consensus on international cybercrime laws.
- MLATs and Slow Response Times: MLATs, though crucial for international cooperation, have faced criticism for their slow response times. This sluggishness, often due to legal complexities and varying national laws, hampers the effective tackling of cybercrime across borders.
- Cloud Act and E-evidence Issues: The Cloud Act in the U.S. and E-evidence in the EU, both aimed at enabling law enforcement to access data across borders, have been criticized for infringing on human rights. These laws exemplify the difficulty of balancing international cooperation with the protection of individual rights.
- Misuse of INTERPOL's Red Notice System: There have been documented cases of countries like China and Bahrain misusing INTERPOL's Red Notice system to politically repress dissent under the guise of fighting cybercrime. This misuse reflects the challenges of ensuring that international cooperation mechanisms are not exploited for political gains.
Cybercrime as an Organized Activity
Cybercrime has evolved over the last two decades, transitioning from lone actors to sophisticated groups primarily driven by financial gain. These groups often mirror legitimate corporations in their organization, with various sizes and structures, indicating their complexity and the serious threat they pose.
- Small Groups: These consist of 1-5 members with annual revenues under $500,000. They typically involve multitasking individuals, with roles like coders, support staff, and network administrators, often holding day jobs alongside their criminal activities.
- Medium-sized Groups: With 6-49 employees and revenues up to $50 million, these groups have a more complex structure with additional management layers. An example is MaxiDed, which evolved from a small hosting provider to a bulletproof hosting provider for illicit activities.
- Large Groups: Resembling large corporations, these groups have functional departments and hierarchical structures. They generate over $50 million in annual revenues. A prominent example is the Conti ransomware group, known for its ransomware-as-a-service model and double-extortion techniques.
Impact on Global Cybersecurity Measures
The inherent nature of cybercrime knows no borders, rendering it a global threat that significantly influences how countries formulate their cybersecurity strategies. Here are five notable cyber incidents that have had a worldwide impact:
- WannaCry Ransomware Attack (2017): Paralyzed over 200,000 computers across 150 countries, affecting healthcare systems and businesses. Highlighted the need for updated systems and international collaboration in cybersecurity.
- SolarWinds Hack (2020): A sophisticated supply chain attack, impacting major US government agencies and businesses. It underscored vulnerabilities in third-party software and the necessity of supply chain security.
- NotPetya Attack (2017): Initially targeted Ukraine but quickly spread globally, causing billions in damages. Demonstrated the destructive potential of malware and the importance of robust digital infrastructure.
- Microsoft Exchange Server Hacks (2021): These breaches affected at least 30,000 organizations globally, emphasizing the need for robust cybersecurity practices in widely used software.
- Colonial Pipeline Ransomware Attack (2021): This attack on a major US fuel pipeline showcased the potential of cyberattacks to disrupt critical infrastructure and the economy.
To combat cyber threats effectively, international cooperation and intelligence sharing are imperative. Check Point Research has reported a noteworthy surge in global cyberattacks in 2022, with data indicating a 38% increase compared to the previous year. For instance, Europol's 2020 Internet Organised Crime Threat Assessment (IOCTA) report reflects the effectiveness of international collaboration in dismantling cybercriminal networks.
Emerging Threats and Future Trends
1. Artificial Intelligence in Cyber Attacks
Artificial Intelligence (AI) has not only transformed how we live but has also been harnessed by cybercriminals to launch sophisticated attacks. AI-powered malware can adapt and evolve in real time, making it challenging for traditional cybersecurity measures to keep up. Understanding the potential of AI in both offense and defense is crucial for countries seeking to fortify their digital defenses.
2. The Growing Complexity of Cybercrime
Cybercriminals continue to innovate, creating increasingly complex attack vectors. Ransomware attacks, data breaches, and phishing scams have grown in scale and sophistication. The best countries for cybersecurity will be those that invest in robust technical defenses and cybersecurity education and training to mitigate the human element of cybercrime.
3. International Collaboration for Cybersecurity
In an interconnected world, no country can stand alone in the battle against cyber threats. International collaboration is paramount. Sharing threat intelligence, coordinating responses, and establishing norms and rules in cyberspace are essential steps to creating a more secure digital environment.
Personal and Organizational Cybersecurity Measures
Whether you're an individual user or part of an organization, cybersecurity is paramount. For individuals, it's about safeguarding personal information, financial assets, and digital privacy. Meanwhile, organizations face the dual challenge of protecting sensitive data and maintaining the trust of their customers and stakeholders. The consequences of cybersecurity breaches can be severe in both cases, ranging from financial losses to reputational damage.
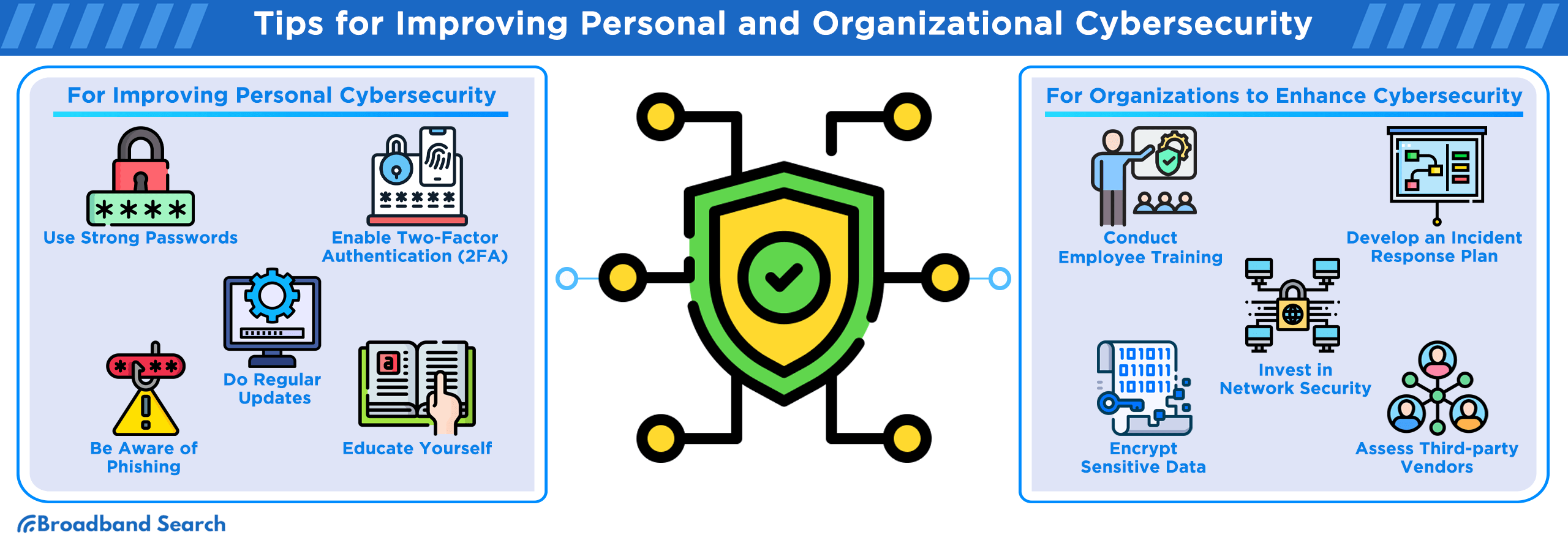
Tips for Improving Personal Cybersecurity
Now, let's talk about the five most effective tips to enhance your personal cybersecurity:
- Strong Passwords: Utilize complex, unique passwords for each online account and consider using a password manager for convenience and security.
- Two-Factor Authentication (2FA): Enable 2FA wherever possible to add an extra layer of protection to your accounts.
- Regular Updates: Keep your operating systems, software, and applications updated to patch vulnerabilities.
- Phishing Awareness: Be vigilant about email and website links, and avoid sharing sensitive information with unsolicited sources.
- Educate Yourself: Stay informed about the latest cybersecurity threats and best practices to remain proactive in your defense.
Strategies for Organizations to Enhance Cybersecurity
For organizations, bolstering cybersecurity requires a multifaceted approach. Here are the five most effective strategies:
- Employee Training: Conduct regular cybersecurity training to educate employees on safe practices and recognize potential threats.
- Incident Response Plan: Develop a robust incident response plan to mitigate the impact of a breach and facilitate a swift recovery.
- Network Security: Invest in advanced network security solutions to detect and prevent intrusions.
- Data Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.
- Third-party Assessment: Regularly assess the cybersecurity posture of third-party vendors and partners to ensure their practices align with your security standards.
Wrapping Up
We've uncovered a landscape where digital defenses vary greatly. Some nations excel in fortifying their online realms, while others face ongoing challenges. And as the digital world evolves, so do the threats, with AI-driven attacks and increasingly complex plots leading the charge.
Amidst this dynamic landscape, international cooperation remains crucial, transcending borders in the fight against cyber threats. Yet let's not forget the role of individual responsibility, where your proactive efforts in personal cybersecurity can contribute to the collective resilience of our connected world. While coalitions work against cybercriminal collectives, you need to make sure to protect your own devices.
FAQ
What role do international cybersecurity laws play in shaping national cybersecurity standards?
International cybersecurity laws shape national standards by establishing guidelines for information sharing, cooperation, and response, fostering a global framework for cyber defense.
How do cybersecurity measures differ in developing vs. Developed countries?
Cybersecurity measures differ in developing countries, often lagging due to limited resources and awareness. Developed nations are more able to invest in advanced technologies and training.
How do national cybersecurity strategies influence global cybersecurity trends?
National cybersecurity strategies influence global trends as successful approaches are adopted by other nations, driving innovation and cooperation in the ever-evolving cyber landscape.
How does cybersecurity affect personal privacy and data protection laws?
Cybersecurity affects personal privacy by balancing protection against surveillance. Data protection laws aim to safeguard personal information while enabling digital security.
What are the most common types of cyber threats faced by countries with poor cybersecurity?
Countries with poor cybersecurity face potential threats to their infrastructure, information leaks, and sabotage. By exploiting vulnerabilities in inadequate defenses, enemies can weaken a country and negatively affect the population.

