The number of websites populating the internet is increasing exponentially, and while this has led to a treasure trove of information and services at our fingertips, it has also opened the door to a multitude of cyber threats. A staggering statistic from Google indicates that nearly 100 million unsafe browsing warnings are showcased to users every week. This illustrates the vast landscape of potentially harmful sites lurking just a click away. It's no longer a luxury but a necessity to be well-informed and cautious about which websites to trust and which ones to avoid.
Ensuring the safety of a website is crucial not just to protect our devices from malware or viruses, but also to guard our personal and financial information from falling into the wrong hands. Whether you're shopping online, reading news, or just browsing, understanding how to discern a website's credibility can be the difference between a secure online experience and a disastrous one. In the following guide, we'll outline steps and tools to help you determine the safety of any website you encounter.
The Importance of Internet Safety and Consequences of Malicious Websites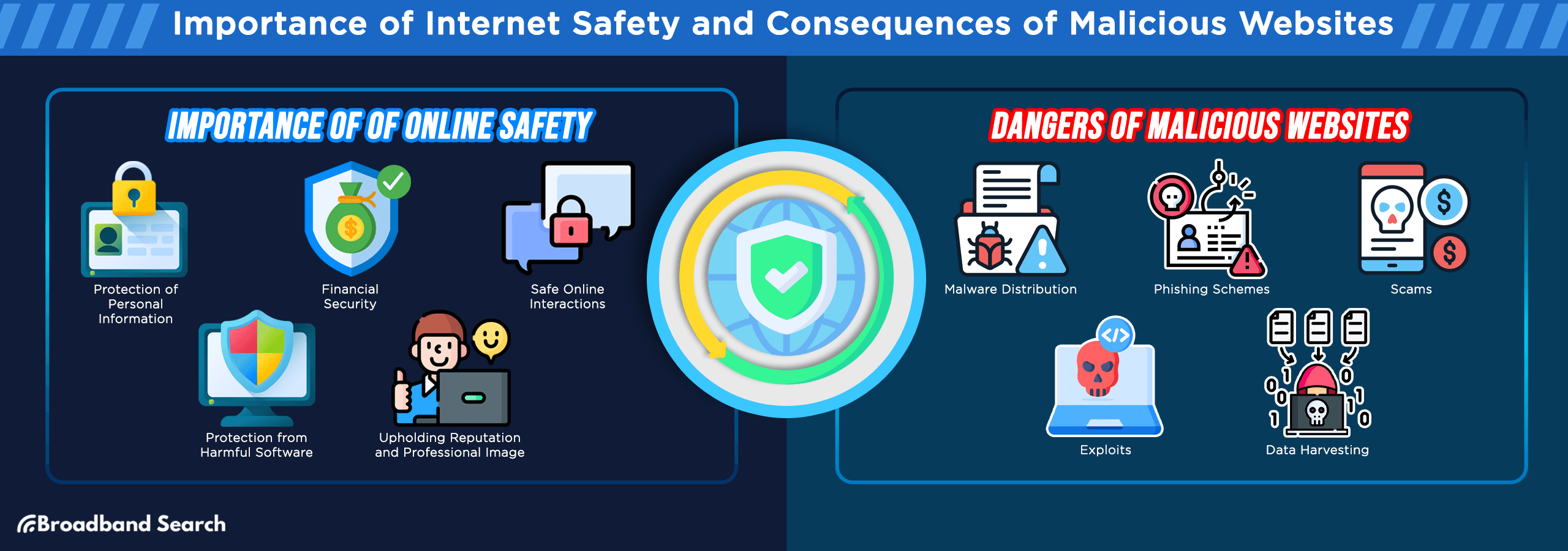
In a world where a significant portion of our lives is spent online, ensuring internet safety isn't just about avoiding digital inconveniences—it's about safeguarding our lives, our privacy, and our assets. Every visit to a malicious website has the potential to inflict severe consequences, making it crucial to understand why internet safety matters.
Imperative of Online Safety
- Protection of Personal Information: Every time you sign up for an account, make a purchase, or fill out a form online, you are potentially offering your personal information. Safe websites ensure this data is encrypted and stored securely. On the other hand, malicious sites may steal this data, leading to identity theft, unauthorized transactions, or worse. Ensuring that you're interacting with a secure website can prevent sensitive information like addresses, phone numbers, and social security numbers from falling into the wrong hands.
- Financial Security: Online shopping and banking have become the norm for many, offering unmatched convenience. But this also means our financial details, including credit card numbers and bank account information, are frequently entered online. Malicious websites can capture this data, leading to unauthorized purchases, drained bank accounts, or compromised financial health. Ensuring that a site uses secure transaction methods and encrypted connections is essential.
- Safe Online Interactions: Social media platforms, forums, and chat rooms can be a haven for cyberbullies, scammers, and predators. While these platforms themselves may be safe, interactions can turn sour without proper precautions. It's crucial to ensure that personal details aren't easily accessible and to be cautious about who you're interacting with.
- Protection from Harmful Software: Malicious websites often host or lead to harmful software like malware, spyware, ransomware, or viruses. These can not only damage or slow down your device but can also spy on your activities, steal data, or lock up your files until a ransom is paid. Having up-to-date security software and ensuring that you're visiting safe sites can significantly mitigate these risks.
- Upholding Reputation and Professional Image: In the professional world, a single mistake like sending data over an unsecured website or falling for phishing schemes can tarnish your image. Businesses also face significant threats—data breaches can lead to loss of trust, legal repercussions, and financial losses. By prioritizing online safety, professionals and businesses can uphold their reputation and maintain the trust of clients and partners.
The Dangers of Malicious Websites
- Malware Distribution: Malware, short for "malicious software," includes a range of harmful programs, from viruses and worms to trojans and ransomware. Malicious websites can automatically download and install malware onto your device without your knowledge, merely by visiting the site. Once installed, malware can corrupt files, spy on your activities, or even take control of your device.
- Phishing Schemes: Phishing websites masquerade as legitimate sites to deceive users into providing sensitive information. For example, you might receive an email that appears to be from your bank, urging you to log in due to a security concern. The link in the email directs you to a fake website identical to your bank's actual site. Unsuspecting users enter their login credentials, which are then captured by cybercriminals.
- Scams: There are countless online scams designed to cheat users out of money or goods. These can range from fraudulent online stores selling non-existent products to advanced fee scams promising large sums of money in return for a "small initial payment." Malicious websites can be set up explicitly to facilitate these scams, luring in victims with too-good-to-be-true offers or fake testimonials.
- Exploits: Exploit websites take advantage of vulnerabilities in software, browsers, or operating systems. When a user visits such a site, the website automatically exploits a security flaw, gaining unauthorized access to the user's device. From there, attackers can install malware, steal data, or even gain full control of the system.
- Data Harvesting: Some malicious websites are designed to covertly gather user data. This doesn't just refer to personal or financial information entered into forms. Sophisticated tracking scripts can monitor your browsing habits, record keystrokes, and even access files or data from your device. This harvested data can be sold on the dark web or used in targeted attacks against individuals or organizations.
Understanding the Basics of Web Security
It is crucial to understand the fundamentals of web security in order to safely navigate the digital world. As the internet grows, it brings both vast information and potential threats. Web security acts as a protective barrier against these threats, from encryption protocols to defensive software. By grasping these foundational concepts, we ensure our online safety and contribute to a more secure internet for everyone.
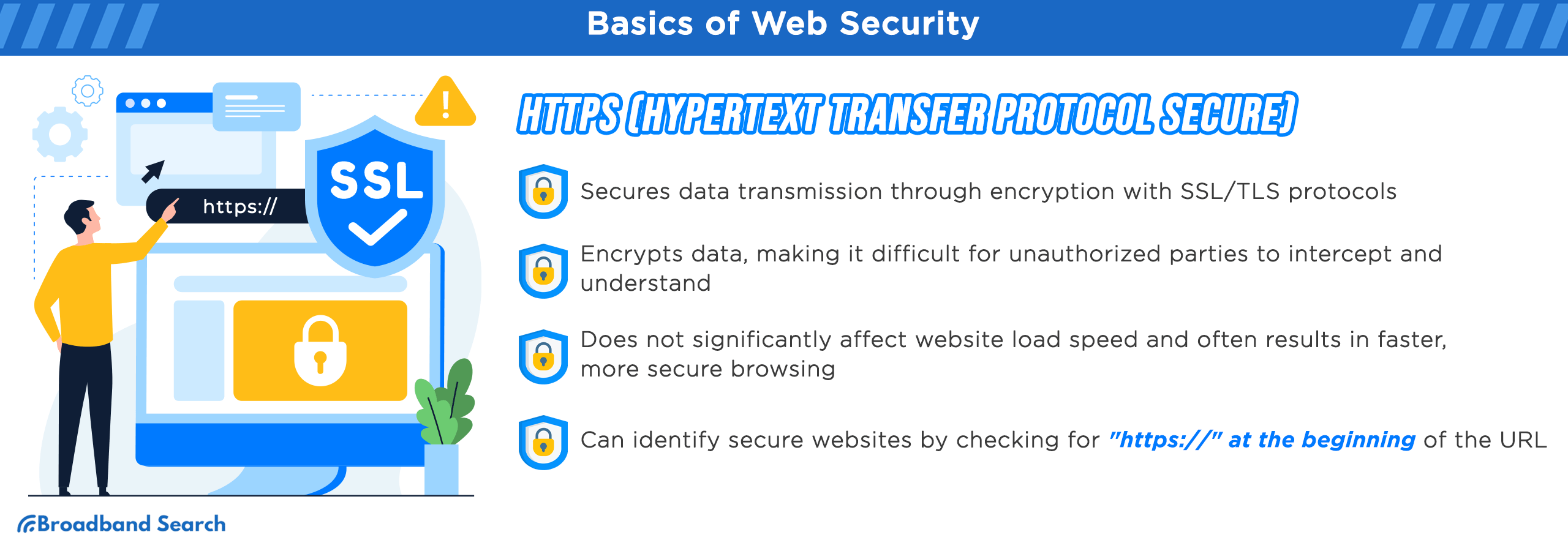
Recognizing HTTPS vs. HTTP
- Security Layer: HTTPS stands for Hypertext Transfer Protocol Secure. The "Secure" part comes from the use of SSL/TLS (Secure Socket Layer/Transport Layer Security) protocols, which provide a secure channel for data transmission. This additional security layer ensures that any data sent or received is encrypted and thus much more difficult for unauthorized parties to intercept or understand.
- Data Encryption: One of the primary benefits of HTTPS is that it encrypts the data sent between the user and the server. This means that even if a hacker were to intercept the data, they would not be able to decipher it easily due to the encryption in place. For example, if you're entering credit card details on an HTTPS website, these details are encrypted so that only the intended recipient (the website server) can decrypt and understand them.
- URL Indication: One of the most straightforward ways to identify whether a site uses HTTPS or HTTP is by looking at the beginning of the website's URL. An HTTPS site will start with "https://" (e.g., https://www.example.com), while an HTTP site will start with "http://". Always ensure that websites, especially those where you input sensitive information, begin with "https://".
- Certificate Verification: When you access a website using HTTPS, the site presents a certificate as proof of its authenticity. Your web browser verifies this certificate with a Certificate Authority (CA) to ensure it's valid and that the website is who it claims to be. If the certificate cannot be verified, your browser will typically display a warning, signaling that the site might not be trustworthy.
- Performance and Load Speed: There's a common misconception that HTTPS websites are significantly slower than HTTP because of the encryption process. While there was some truth to this in the early days of the web, advancements in technology and optimizations have made the difference in load speed almost negligible for most users. In fact, many modern web optimization techniques and protocols, like HTTP/2, work exclusively with HTTPS, which can make secure websites even faster than their non-secure counterparts.
The Role of Domain Names
- Top-level Domains (TLDs): Top-level domains (TLDs) are the final segments in domain names, like .com, .org, or .net. Serving as essential parts of the internet's domain name system, they give insights into a website's nature or origin. For instance, TLDs like .gov and .edu are exclusive to government entities and educational institutions, respectively. Moreover, TLDs are pivotal in the DNS lookup process. When a user types a domain, such as 'google.com', DNS resolvers initiate their search at the TLD level, guiding them to the correct origin server's IP address.
- Second-level Domains (SLDs): Positioned immediately to the left of the top-level domain (TLD), the SLD is often the most recognizable part of a web address. For instance, in the domain "google.com", while ".com" is the TLD, "google" is the SLD. It predominantly symbolizes the actual domain name, which can be a brand, business, or organization, serving as the primary identifier for users seeking that particular website.
- Subdomains: Subdomains are specific segments found to the left of the second-level domain, helping to further categorize and direct users within a broader website. For instance, in the domain "mail.google.com", while "google" is the second-level domain, "mail" stands as the subdomain. These subdomains not only facilitate a structured approach to website organization but also streamline navigation, ensuring users can access different services or sections with ease.
Using Online Tools and Services
There are different tools and services tailored to navigate the complexities of the online realm, each designed to address distinct challenges and threats. Just as a craftsman relies on a set of specialized instruments, internet users benefit immensely from a diverse toolkit when venturing online. These tools not only bolster security but also enhance the overall browsing experience, making the web both a safer and more efficient space.
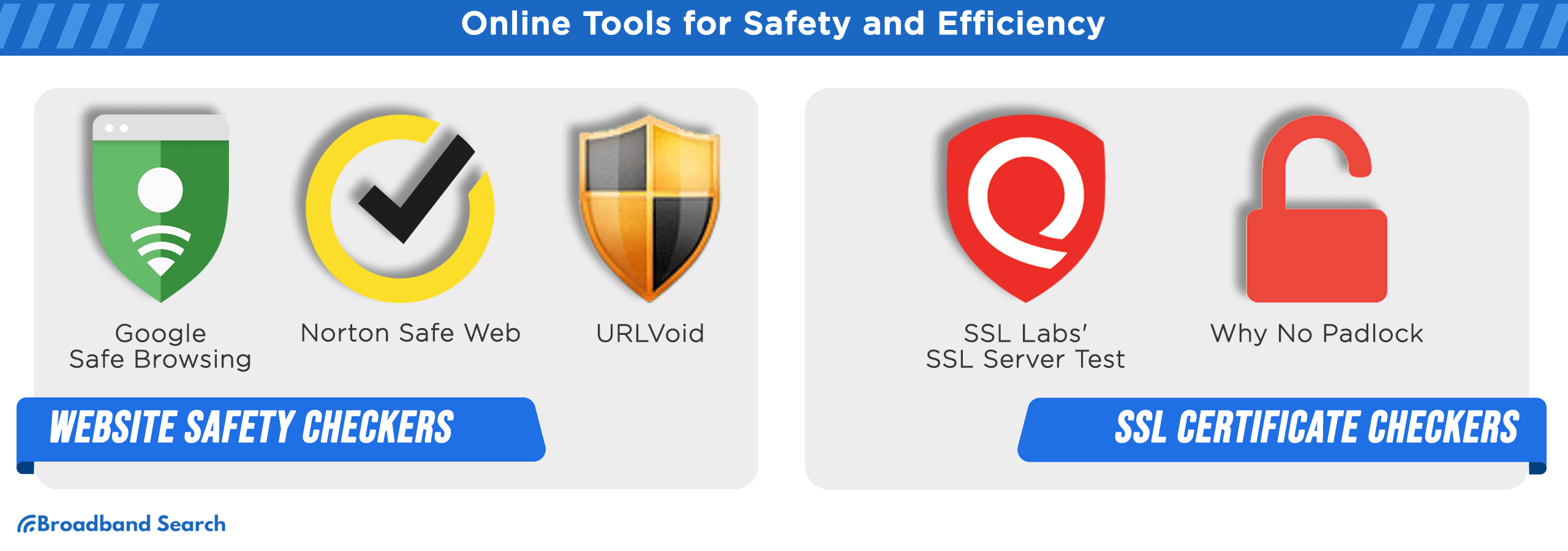
Website Safety Checkers
Website Safety Checkers are invaluable allies in the digital realm, dedicated to safeguarding users from malicious content. These tools vigilantly evaluate websites, providing both early detection of potential threats and frontline defense. With benefits like immediate alerts on websites with harmful content and regular database updates to counter evolving cyber threats, they ensure users navigate the web with confidence.
Popular tools:
- Google Safe Browsing: A powerhouse by Google, it screens websites against an extensive database of reported phishing and malware-infected sites.
- Norton Safe Web: Norton Safe Web, created by Symantec Corporation, assists users in detecting harmful websites. This service provides website information through automated assessments and user input.
- URLVoid: Utilizing an array of blacklist engines and online reputation resources, it provides a comprehensive safety verdict for websites.
SSL Certificate Checkers
SSL (Secure Socket Layer) certificates are fundamental to ensuring online security, serving as a testament to a website's commitment to safeguarding user data. These certificates not only provide robust encryption, ensuring that the data exchanged between users and servers remains shielded from prying eyes but also bolster a site's credibility, inspiring trust among visitors.
Tools for checking SSL certificates:
- SSL Labs' SSL Server Test: This tool delves into the intricacies of a website's SSL configuration, revealing any potential weaknesses or misconfigurations.
- Why No Padlock: Tailored to identify issues that might break or compromise a site's SSL status, ensuring the integrity of the website's security indicators.
Evaluating Website Content
How do you discern the credibility of a website amidst the vast ocean of information available online? The process involves more than just a cursory glance at the webpage's design or its domain name. Proper evaluation demands a critical assessment of the content presented, its sources, and its relevance to the intended query. By adopting a systematic approach to content evaluation, users can sift through the noise, ensuring they consume and rely on information that is both accurate and trustworthy.
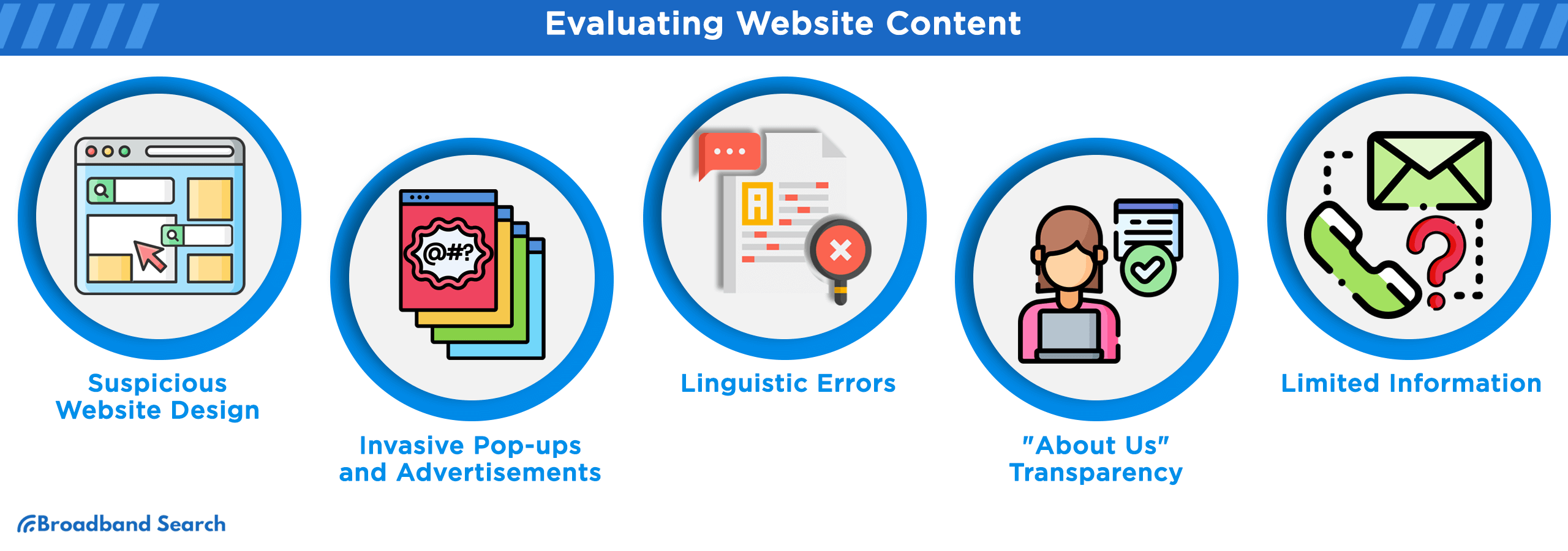
Spotting Red Flags in Website Design and Content
- Questionable Design: Sites with an unprofessional, outdated, or chaotic design can often be a telltale sign of a scam or low-quality platform. These sites might have been hastily constructed without much thought or investment.
- Invasive Pop-ups and Advertisements: A legitimate, user-focused website aims to provide a pleasant browsing experience. Conversely, sites that bombard users with aggressive ads, unsolicited pop-ups, or intrusive notifications may have ulterior motives, ranging from earning ad revenue at the user's expense to harboring malicious software.
- Linguistic Errors: Consistent linguistic mistakes, such as poor grammar, spelling errors, or oddly phrased sentences, can be indicative of a website's unreliability. While occasional typos can happen anywhere, a pattern of linguistic negligence often suggests a lack of professionalism or, in some cases, a site created by non-natives for scam purposes.
Checking the "About Us" and "Contact" Sections
- Transparent Information: Legitimate websites usually have an "About Us" section detailing their mission, team, history, and objectives. A vague or nonexistent "About Us" section can be suspicious.
- Contact Details: A genuine website will offer clear contact information, including a physical address, phone number, and email. Websites that only provide a generic contact form without any accompanying contact details might be hiding something or not invested in customer interaction.
Reviews and Reputation
To assess the credibility of a website, examining its reviews and reputation is key. In an era of abundant digital information, genuine user testimonials and ratings from trusted organizations help distinguish authentic platforms from untrustworthy ones. These insights, reflecting user experiences and ethical standards, are pivotal in guiding online decisions and interactions.
The Power of User Reviews
User reviews have emerged as potent tools for gauging the credibility of online platforms. These reviews, penned by real users, provide firsthand accounts of experiences, highlighting both the strengths and potential red flags of a website.
- Insight into Legitimacy: Whether it's praise for excellent service or complaints about poor product quality, user reviews shed light on the authenticity and reliability of a website. A consistent pattern of negative feedback or issues can serve as a warning to potential users.
- Sources for Reviews: While reviews can be found on many platforms, it's essential to consider feedback from trustworthy sources. Websites like Trustpilot, SiteJabber, and Google Reviews are renowned for hosting genuine user reviews, making them reliable platforms for gathering user insights.
The Role of the Better Business Bureau (BBB) and Similar Organizations
Beyond individual user reviews, established organizations dedicated to assessing and rating businesses play a pivotal role in establishing website credibility.
- Evaluation Methods: Organizations such as the BBB employ comprehensive methods to evaluate businesses. They consider multiple factors, including customer feedback, the history of complaints, transparency in business operations, and overall business practices, to form a holistic view of a company's credibility.
- Ratings as Indicators: The BBB, among others, provides ratings that serve as quick indicators of a business's trustworthiness. A high rating or accreditation from such an organization is often a testament to a website's commitment to ethical practices, customer satisfaction, and transparency. Users can use these ratings as benchmarks when considering the legitimacy of a website or business.
Additional Protective Measures
Beyond the tools and reviews that aid in website evaluation, there's an array of additional measures that individuals can adopt. These supplementary strategies not only reinforce security barriers but also empower users with knowledge and tools, fortifying their defenses against evolving digital threats. Whether it's employing advanced software solutions or simply being aware of the latest online scams, these additional measures serve as robust layers of protection, ensuring a safer digital experience.
Keeping Your Browser and Antivirus Updated
- Regular Updates: Continually updating your browsers and antivirus tools is vital. These updates equip tools with the latest protective features, enhancing their ability to combat ever-evolving cyber threats and ensuring a shielded online experience for users.
- Defense against Threats: Every software update is an enhancement of defense mechanisms, fixing vulnerabilities previously identified. By staying up-to-date, users amplify their resistance against new threats, ensuring a secure digital environment.
Using Web Security Extensions
The following extensions are designed to shield users from diverse online threats, ensuring a browsing experience that is both secure and efficient.
- uBlock Origin: Renowned for its efficiency, this open-source browser extension is used for filtering content, notably for blocking ads. This extension can be integrated with browsers such as Chrome, Chromium, Edge, Firefox, Opera, Pale Moon, and Safari versions preceding 13.
- HTTPS Everywhere: Developed by the Electronic Frontier Foundation (EFF), this extension encrypts your interactions with numerous prominent websites, enhancing the safety of your browsing experience.
- WOT (Web of Trust): WOT safeguards your online experience by alerting you to potential threats such as harmful links, scams, malware, and phishing attempts. WOT showcases circular indicators reflecting the safety ratings of every website you access, as well as hyperlinks leading to other websites.
Scrutinizing the URL
- Look Beyond the Domain Name: Cybercriminals craftily use minor misspellings or slightly altered versions of popular domain names to trap users. Such subtle alterations, often overlooked, can lead users to malicious sites, exposing them to various online threats.
- Check the Domain's Age: While a fresh domain isn't automatically dubious, if it represents itself as an age-old, trusted brand, caution is advised. Such discrepancies can be signs of fraudulent intentions or mimicry.
- Avoid Clicking on Shortened URLs Blindly: Services like Bitly compress lengthy URLs for convenience. However, this shortening can conceal the true nature of the link. Tools such as CheckShortURL allow users to view the complete URL, ensuring informed and safe clicks.
Be Wary of Unsolicited Communication
- Unexpected Emails or Messages: The starting point of many phishing schemes is an unsolicited message or email. These often prompt users to act swiftly, pushing them to click a dubious link or download a suspicious attachment.
- Verify Before You Act: Should you get a message that seemingly comes from a bank or similar institution, it's imperative to authenticate its legitimacy. Instead of replying directly, reach out to the institution via its official contact methods to confirm.
Double-Check Download Sources
- Official Sources: The internet is a vast repository of software and apps. However, to ensure safety and avoid potential malware, it's crucial to source downloads only from the official websites or platforms that have earned user trust.
- Beware of "Too Good to Be True" Offers: Attractive offers, like free versions of typically pricey software, can be tempting. However, these alluring propositions, especially from lesser-known sites, can sometimes conceal malware, making the user's system vulnerable to attacks.
The Takeaway
The internet is teeming with various scams, and chances are you have encountered one unknowingly. While the internet gives us many helpful tools and information, there are also people who try to trick us. These scams can appear as normal emails or websites that look safe. As the internet keeps changing, the tricks people use to scam others also change.
It is very important to be careful and know what's safe and what's not. We need to learn more, be alert, and always think twice before clicking on something or sharing our details. By staying aware and being smart online, we can enjoy all the good things the internet offers and avoid the bad ones.
FAQ
How can I protect my online identity?
- Use strong, unique passwords.
- Enable two-factor authentication.
- Be cautious about sharing personal information online.
- Regularly update your devices and software.
- Use a reputable antivirus program.
- Avoid clicking on suspicious links or emails.
- Monitor your online accounts for unusual activity.
Are all public Wi-Fi networks unsafe?
Not all public Wi-Fi networks are unsafe, but many lack robust security. It's advisable to use a virtual private network (VPN) when connecting to public Wi-Fi to encrypt your data and enhance security.
How often should I update my passwords?
Passwords should be updated regularly, ideally every few months. It's crucial to change them immediately if you suspect a breach or if a service you use has been compromised.
What is two-factor authentication?
Two-factor authentication (2FA) is an extra layer of security for your online accounts. It requires you to provide two different forms of verification (e.g., a password and a temporary code sent to your phone) to access your account, making it more secure.
Are cookies dangerous?
Cookies themselves are not inherently dangerous. They are small text files that websites use to store information about your browsing. However, some cookies can track your online activity, which raises privacy concerns. Most modern browsers allow you to manage and delete cookies for better control over your privacy.

